The biggest threat to many companies is not the actions of a single hacker, but a network of compromised devices controlled from a remote location. A constant stream of data packets is hurled at your systems by thousands of attackers from all over the world. One of our customers was subjected to this threat in the form of a massive DDoS attack. This attack deserves special attention due to its size, speed and complexity.
The escalation of the attack
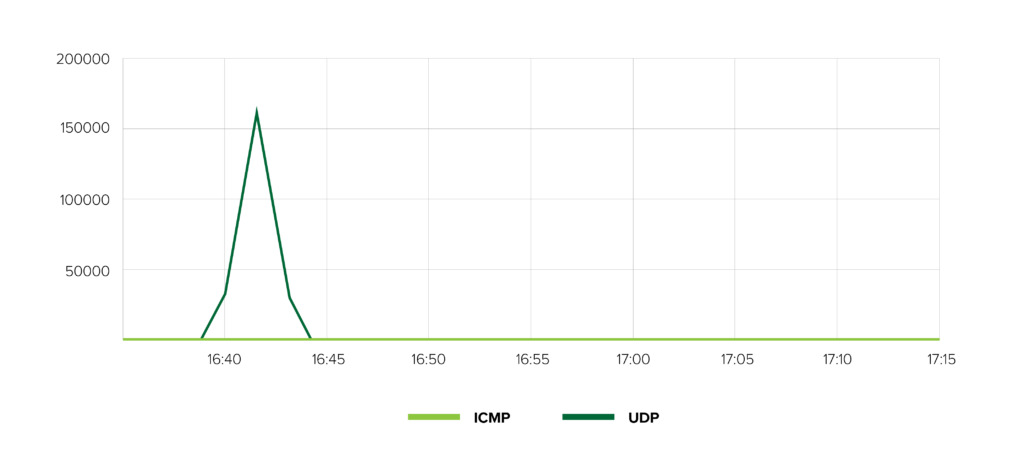
The attack lasted for several days and was characterized by unprecedented speed and intensity. As the following graph shows, the data rate rose from 25 Mbit/s to an impressive level of 163,000 Mbit/s in just two minutes. This rapid escalation can overwhelm even high-performance networks and illustrates the increasing complexity and professionalism of cyber attacks.
Geographic distribution and complexity
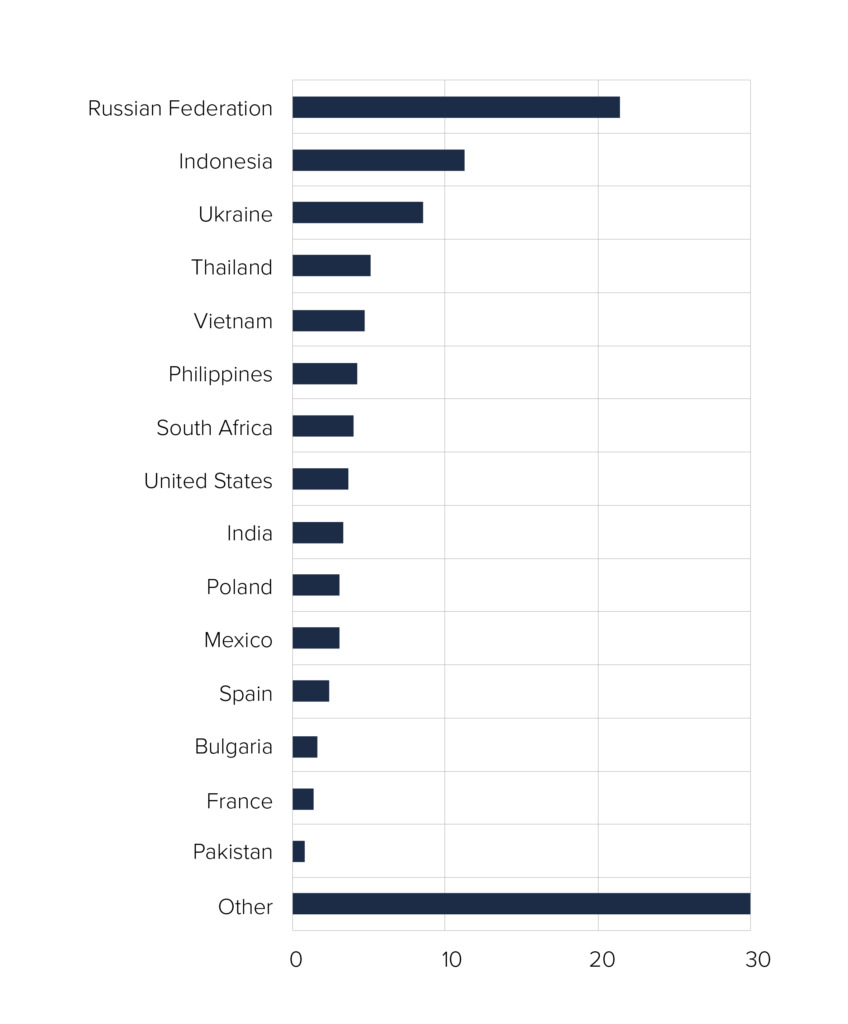
The geographic distribution of the attack across 146 countries, with a particularly high proportion from Russia (21%), suggests a well-organized and far-reaching botnet. The distribution of attack traffic across various scrubbing centers, including locations in Asia and North America, illustrates the complexity of the attack routes. The fact that even less busy locations such as Hong Kong and New York were involved in the attack itself suggests a high degree of planning and coordination.
The geographic diversity makes it difficult to analyze the origin of the attack and makes it difficult to identify the exact motives of the attackers. The strikingly wide distribution of attacks (large proportion from “other” sources) suggests that the attackers deliberately tried to cover their tracks. Nevertheless, the geographical distribution of the attack could be an indication that this could have been a politically motivated attack.
The technical details of the attack were as follows:
UDP floods, in which a large number of UDP packets are sent to random or specific ports with the aim of overloading network connections and server resources. The User Datagram Protocol (UDP) is a connectionless protocol that does not require confirmation of receipt. A high rate of packet loss, difficult processing of legitimate packets and the risk of a potential service crash can be observed.
DNS amplification: fake DNS queries were sent to public DNS resolvers with a fake source IP. This directed a large amount of response data to the target. An exponential increase in data traffic and an overload of the target and potentially also of the DNS resolvers can be observed.
IP fragmentation to make packet filtering more difficult. To do this, large data packets were split into smaller fragments. This results in increased CPU utilization on the target system and makes it more difficult to detect attack patterns.
Learn more about a GDPR-compliant, cloudbased and patented DDoS Protection that delivers, what it promises.
The botnet
Analysis of the attack patterns suggests that this is a highly organized botnet with over 70,000 compromised devices. The immense number of infected machines, distributed across numerous Internet service providers worldwide, underscores the professional nature of the attack. The highly diversified origin of the attack vectors makes identifying and isolating the botnet considerably more difficult. It can be assumed that the attackers have access to an extensive infrastructure that enables them to maintain their activities over a longer period of time and to conceal their identity.
Possible motives and challenges
The reasons for this large-scale attack are varied and could be financially or politically motivated. Possible scenarios include:
- Blackmail: The attacker may have tried to force the victim to pay a ransom.
- Competition: A competitor may have tried to damage the victim’s business.
- Political motivation: Russia’s involvement in the attack raises speculation about possible political motives.
Conclusion
Defending against this attack posed a significant challenge. The combination of UDP floods, DNS amplification and fragmentation of data packets made it difficult to isolate and block the attack. The use of numerous smaller packet sizes also made it difficult to filter legitimate traffic. The attackers apparently tried to overload the defense systems and create the broadest possible attack surface. The distribution of attacks across different countries and the use of a large number of IP addresses illustrate the complexity of the attack and the difficulties in identifying the attackers.
This DDoS attack illustrates the increasing threat of cyber attacks. Consequently, companies are obliged to continuously adapt their security measures to current conditions and invest in robust DDoS protection solutions. Close cooperation with experienced security experts is essential.
Do you want to effectively protect your company from DDoS attacks? We offer comprehensive solutions to secure your IT infrastructure. Contact us today for a personalized consultation.
The world of cybersecurity includes a wealth of opportunities and challenges in which women are playing an increasingly important role. But, as in many other industries, women often face unique obstacles and have to deal with specific threats, especially in light of the industry’s rapid expansion. In a recent (German) podcast conversation between Lisa Fröhlich, Link11’s corporate spokesperson, and Julia Dudenko, Group CISO at Haniel, some insights were shared that illustrate how women are facing threats while capitalizing on opportunities in this fast-paced and dynamic environment.
From training to security strategy
The conversation began with a look at the importance of early education in cybersecurity. Julia Dudenko emphasized the need to raise awareness of cybersecurity in society, especially among children and young people. She emphasized that the diversity of professions in the cybersecurity industry is often not sufficiently explained and that it is important to get young people excited about this exciting career opportunity at an early age.
Lack of role models, gender stereotypes and prejudices – what do women face in the industry?
Another important point of discussion was the challenges faced by women in the cybersecurity industry. Current statistics show that women are still severely underrepresented, especially in management positions. This is reflected not only in the gender distribution but also in the salary differences between male and female professionals.
The Group CISO of Haniel shared her personal experience as one of the few women in a technical leadership position and emphasized the positive aspects, such as clear feedback mechanisms and increased visibility. Being the only woman in the room also has clear advantages.
Where is the journey in cyber security heading?
The discussion concluded with an outlook on future trends and developments in cybersecurity. Julia Dudenko expressed how the nature of threats has changed over time and how important it is to continuously adapt in order to respond to new challenges.
Traditional security measures are often no longer sufficient to fend off complex attacks such as ransomware, phishing, and advanced persistent threats (APTs). Women in cybersecurity may or may not have technical expertise needed to plan for these threats. More important in the CISO role is a deep understanding of business processes and the evolving threat landscape and the resulting risks. It also helps to be able to present the threats in a comprehensible manner, to quantify them financially, and to act proactively.
The experienced IT security expert also highlighted the importance of AI-supported security solutions to identity protection and combat personalized attacks. She also explained the need to prepare for new challenges, such as quantum computing, and the need for continuous training to keep pace with the ever-changing threat landscape.
Conclusion: An exciting and dynamic industry
The podcast conversation between Lisa Fröhlich and Julia Dudenko provided a fascinating insight into the world of cybersecurity and the role of women in this industry. The future of cybersecurity is increasingly in their hands, and so it is crucial that they receive the support and encouragement they deserve. This requires not only a change in corporate culture and practices, but also targeted measures to promote diversity and inclusion in the industry.
Link11 also offers many opportunities to enter the exciting world of Cybersecurity.
It’s time to overcome gender stereotypes and recognize women as equal partners in cybersecurity. By providing mentoring programs, training and education opportunities, companies can help unlock the full potential of female employees in the industry.
Overall, the cybersecurity industry not only offers a variety of career opportunities, but also the chance to have a positive impact on the digital future. Through collaboration, support and engagement, women can help create a safer and more resilient digital world for all.
The year 2023 and cyberattacks are unfortunately closely intertwined. The risk of falling victim to a cyberattack is always present, but the dangers for companies were particularly acute in the last 12 months. Especially when we talk about DDoS attacks.
The hacker group Anonymous Sudan, for example, bombed the chatGPT service provided by Open AI until it was inaccessible for a long time. NoName057(16), another hacker group that carries out cyberattacks under the guise of politics, launched the dangerous DDoSia project to make DDoS attacks freely accessible to anyone interested.
It has also become clear that artificial intelligence (AI) is increasingly being used to control DDoS attacks. This makes the attacks smarter and therefore more dangerous. Conventional protection systems that have not implemented their own AI can be quickly overcome and no longer pose much of an obstacle.
The third quarter of 2023 gave us a taste of the future
Link11 data from the third quarter of 2023 clearly shows that the trend is changing from “classic” DDoS attacks to a smarter, more effective approach. While single-vector attacks and attacks with nine or more vectors decreased, our experts saw a 116% increase in attacks with five to eight vectors.
The figures suggest that cybercriminals are more effective at testing their victims’ systems for vulnerability and are not unnecessarily firing the entire attack load at well-protected targets. Instead, inadequately protected targets are sought out, which are then attacked in a more focused manner. As a result, attacks bounce off defenses much less frequently and now strike in far more worthwhile locations.
ENISA’s latest DDoS situation report is worrying
As it does every year, the European Union Agency for Cybersecurity (ENISA) has published its status report on the current DDoS market situation. ENISA analyzed 310 selected DDoS attacks in the period from January 2022 to August 2023.
The conclusion: attacks are not only increasingly being used as “ammunition for political motivations”, but the threat has also developed into a “massive danger” due to new vectors and attack patterns.
ENISA also points out that DDoS attacks are becoming cheaper, easier, and more aggressive. New players, in the form of surprisingly well-coordinated hacker groups, have entered the playing field and are launching major attacks without having to worry about possible penalties.
The study confirms the findings of our Q3 figures that no one is safe from DDoS attacks. However, a clear shift in attacks towards the public sector can be observed. State administration was the target of 46% of all attacks analyzed. 66% of all attacks were generally politically motivated, and 50% of the analyzed attacks had a direct link to the Russian-Ukrainian war.
One statistic, however, is particularly striking: 56.8% of all analyzed attacks resulted in a complete collapse of the target. Websites or services were no longer accessible; the victim was completely incapacitated on a digital level.
How many companies or organizations suffered at least severe performance losses due to attacks is not detailed in the report. However, it can be assumed that far more than the 56.8% mentioned above at least had to deal with unpleasant consequences – even if the worst-case scenario could be prevented.
Rely on a proven partner
Effective DDoS protection for the public sector should not only be fast and accurate in detecting attacks, but should also strictly comply with EU data protection regulations. Our automated and patented link protection solution fulfills all these points.
During the height of the Covid19 pandemic, we made the basic version of our DDoS protection available free of charge to all public health, government, and educational organizations. Not only did we help many authorities that were victims of cyberattacks at the time, but we were also able to optimize our technology down to the smallest detail for the specific needs of the sector. This means you can benefit from a solution that has already proven itself in the public sector in an absolutely exceptional situation.
A large number of authorities, public-sector companies, and companies in the KRITIS sector, such as German air traffic control, Frankfurt airport operator Fraport AG and energy supplier Mainova, already trust us and our security technology.
Reliable protection saves a lot of headaches
AI-based DDoS protection solutions for IT infrastructures and web applications that develop and improve themselves are the best way to ensure reliable protection. Scalable and automated technology mitigates DDoS attacks of any kind within the shortest possible time and protects you from all attacks around the clock.
Let’s discuss your individual risk prevention strategy together. Start by arranging a non-binding appointment with our security experts to see how we can help.
The Black Friday rush has faded. It’s time to look back on the past few days of bargain hunting and the start of the peak season for retailers in 2023. The Christmas shopping period presents retailers (both online and offline) with a double challenge: managing the rush of shoppers and protecting themselves from increased cyberattacks.
After all, these weeks not only promise record sales but also attract cyber criminals who try to hide behind the increased traffic. Above all, distributed denial-of-service (DDoS) attacks are a serious threat.
Continuous sales growth on Black Friday
According to a Bitkom survey, half of Germans planned which deals they wanted to purchase over the Black Friday weekend. Elsewhere, 63% of consumers wanted to buy both online and offline and take advantage of the offers. A look at the figures makes it clear that Black Friday has become an essential date in the calendar for many bargain hunters.
The shopping event has its origins in the USA. Traditionally, the Friday after Thanksgiving is considered a national bridge day, which has become one of the best-selling shopping days of the year. This year’s sales promotions once again generated record sales of 9.3 billion dollars for Shopify customers over the Cyber Weekend.
Since the online giant Amazon brought the concept to Germany in the mid-2000s with numerous discounts and special offers, Black Friday has similarly developed into a billion-dollar sales driver in this country. According to an analysis by e-commerce specialist Criteo, the shopping mood in Germany was particularly strong compared to other European countries.
Here, traffic increased by 15% and completed sales by 12% compared to the previous year. However, with increasing success, the Cyber Weekend and the subsequent shopping season up to Christmas act like magnets for cyber criminals.
The danger of DDoS attacks
DDoS attacks are one of the most classic threats in the digital space. The strategy is simple and effective: criminals bombard a website with many requests, which overload the server and/or the Internet connection. The consequences are serious: the affected site suffers considerable performance losses or even collapses completely.
For online retailers, it is essential to prevent such a scenario in order to avoid frustration among shoppers, loss of sales, damage to reputation and financial losses.
Five times more DDoS attacks than in the previous year
Link11 figures prove the explosive nature of the issue: the number of attacks on Black Friday weekend increased fivefold compared to the previous year. There were also several noticeable increases in attacks in the run-up to the shopping event. Both six and two weeks before the popular shopping day, a particularly high number of smaller DDoS attacks were recorded in the Link11 network, which could indicate that attackers had launched their first ransom DDoS attacks.
To emphasize their potential claims, there was an increase in attacks shortly before Black Friday, with attack volumes significantly above the monthly average. A look at the third quarter of 2023 also shows that the threat to online retailers is traditionally on the rise.
Smart and efficient – DDoS attacks are becoming more intelligent
The number of DDoS attacks larger than 8.5 Gbps has more than doubled compared to the same period last year. The significant increase of 130% is particularly worrying for small and medium-sized companies. Many of the companies use hosting packages with a performance of 10 Gbps. Internet connections of this size are therefore quickly paralyzed by attacks of this magnitude.
The dynamics of the attacks show an interesting shift. The number of single-vector attacks and attacks with more than nine vectors have decreased in the Link11 network. In contrast, the number of attacks with two to eight vectors has risen significantly. This suggests that attacks are becoming smarter and more efficient – cyber criminals are refining their tactics.
Instead of proceeding indiscriminately with many attack vectors, they are focusing on strategies with fewer – but more promising – vectors. The attackers also test whether a more complex attack is worthwhile. After all, why should they fire all their bullets if they encounter a well-protected system, and the attack is repelled in a matter of seconds?
The German Federal Office for Information Security (BSI) also warned of the danger of DDoS attacks on online retailers back in 2021: new attack technologies could be used more frequently during periods of high turnover. The BSI’s recommendation even then was to adapt protective measures to the increased capacities of the attackers.
What useful protection mechanisms are there for online retailers?
In view of this threat situation, it is essential that online retailers take the risk of DDoS attacks seriously. Major players in e-commerce have implemented comprehensive protective measures for years. However, smaller and less tech-savvy online retailers can find it difficult to effectively protect themselves from increasingly sophisticated cyberattacks. Nevertheless, it is crucial for this target group to familiarize themselves with the most important DDoS protection measures before an emergency occurs.
One preventative measure is to adequately prepare your own e-commerce platform for the expected traffic. Joint forecasts by IT and sales as well as load tests in advance can provide information on whether the existing infrastructure can withstand the requirements. It is not only the pure server capacities that are decisive here, but also the resilience of the network and the applications. Bottlenecks should be identified and rectified at an early stage to ensure a smooth shopping experience for customers.
It is also advisable to outsource static content to content delivery networks (CDNs) to optimize loading times. During peak times, personalized content should also be temporarily deactivated to ensure smooth performance. Comprehensive preparation for potential IT bottlenecks and precise monitoring play key roles in ensuring that e-commerce platforms function optimally, even in times of increased data traffic.
Scalable solutions for DDoS protection
Nevertheless, the conventional expansion of bandwidths and server capacities is reaching its limits. Particularly on days such as Black Friday, when traffic from normal shoppers increases massively anyway, DDoS attacks can cause considerable damage with little effort. This is where cloud-based, scalable DDoS protection solutions come into play.
These solutions are characterized by their ability to adapt to variable requirements in real time. They analyze data traffic, detect anomalies, and block malicious access even before it reaches the site’s infrastructure. By using cloud resources, such solutions can offer almost unlimited scalability.
This means that they can cope with sudden peak loads without any loss of performance. Even in the event of an attack, there is hardly any significant impact on business operations. This technology also enables smaller online retailers to protect themselves on a par with their larger competitors.
DDoS prevention as the key to security
At a time when e-commerce is booming and competition is constantly increasing, the security of online stores is of crucial importance. Especially during the peak shopping season, cyber criminals should not be given the chance to jeopardize the success of retailers. Investing in DDoS prevention is therefore not only sensible, but necessary.
If you have any questions about our Web DDoS Protection or our Secure CDN, please feel free to contact us at any time and arrange a consultation with our security experts.