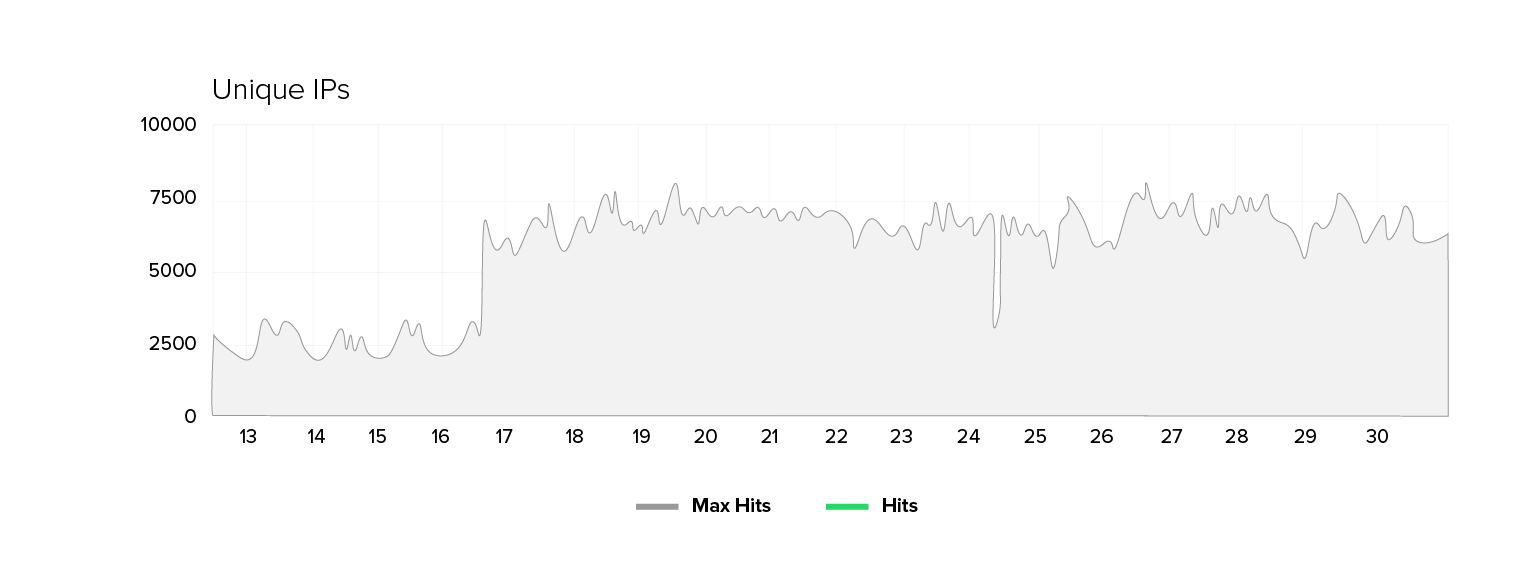
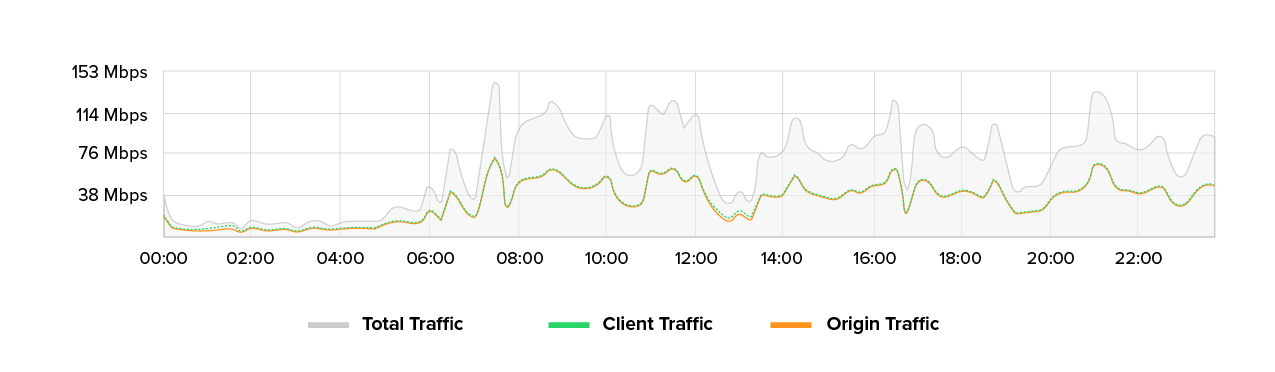
We have been observing an unusual pattern in the IT environment of a public sector customer for quite some time now. The number of unique IP addresses has skyrocketed from 2,000 to 2,500 during peak times to a regular range of 5,000 to 8,000. One would expect a proportional increase in requests and required bandwidth with this doubling of visitor numbers. However, bandwidth and request volume are increasing only moderately (by a factor of 1.3 to 1.7), while the number of unique IPs remains virtually constant.
This is more than a minor statistical detail. It points to a bot-driven pattern with an unexpected structure.
What does this phenomenon look like?
Since the cutoff date, the customer has experienced a sustained increase in unique IP addresses that is not short-lived.
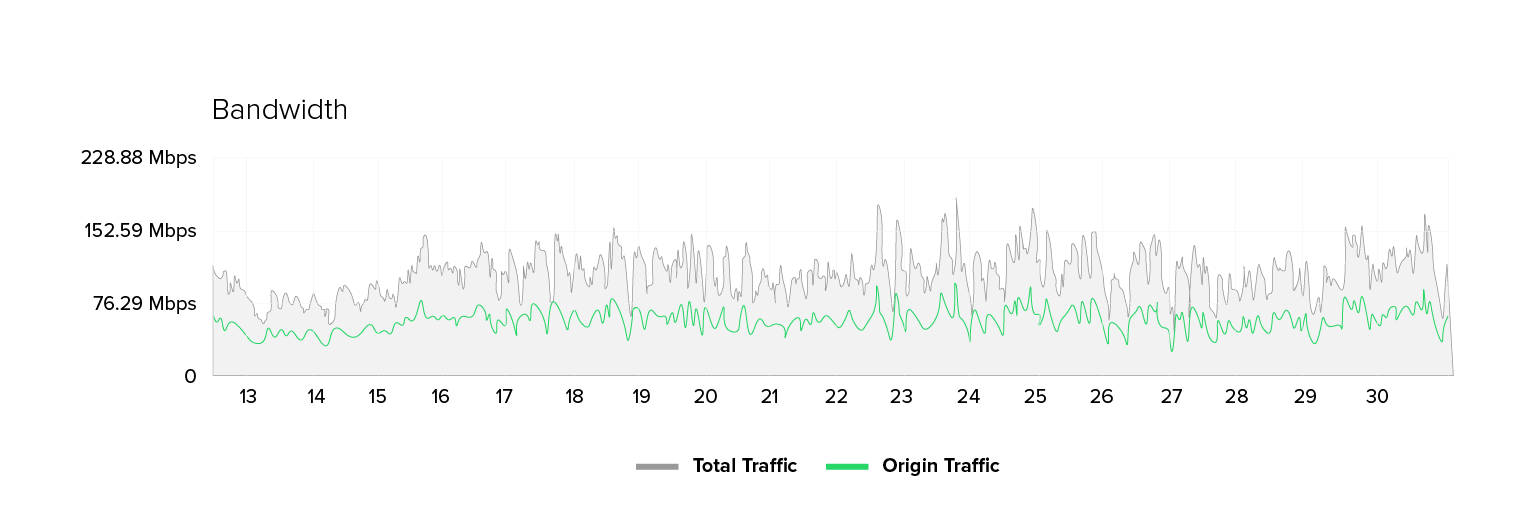
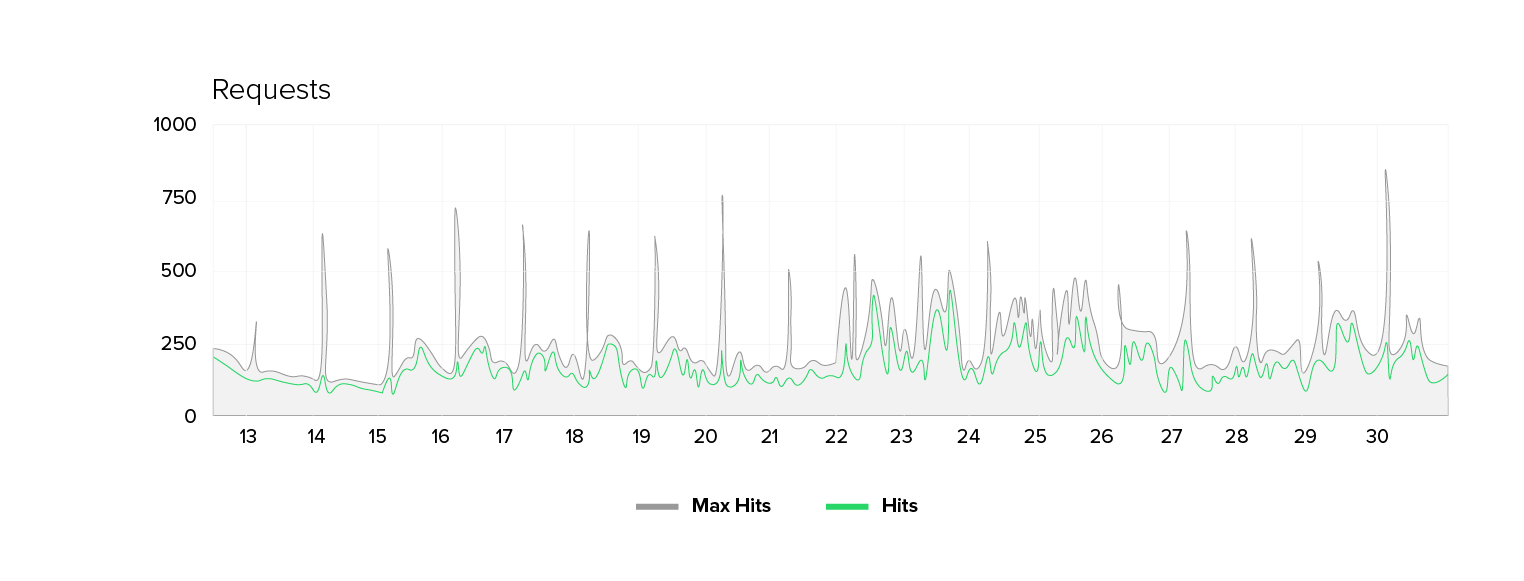
The metrics at a glance: The number of unique IPs has tripled in some places. Yet, the number of requests is increasing by only 50 to 70 percent, and the bandwidth just by 30 to 70 percent. At the same time, we find that the origin server’s response time deteriorates. There are higher average values, more peaks, and occasional 500 errors. Notably, there are no signs of massive content downloads (e.g. images or scripts), and the shift in website traffic profiles is subtle and partly contradictory.
Why is this discrepancy noticeable?
When the number of real users increases, the volume of requests and bandwidth typically rise proportionally. A browser loads not only HTML pages, but also images, fonts, stylesheets, scripts, and videos. This results in a significantly higher load per visit.
Bots behave differently. They are usually interested in the HTML – the “raw text” of the page – and ignore everything necessary for visual rendering.
This explains why the number of unique IP addresses increases dramatically without the bandwidth increasing at the same rate.
- Many bots generate little data per request,
- But when thousands act simultaneously, the result is in a very high connection density.
Although bots that only load HTML generate minimal traffic compared to real browsers, when thousands of them act simultaneously, they can have a significant impact on server resources.
Technical anomalies
- High number of unique IP addresses and moderate bandwidth: The number of unique IP addresses increases by a factor of 2-3 while the bandwidth only increases by a factor of 1.5–1.75.
- Increased server latencies: Origin response times are higher on average and show significantly more peaks.
- Request mix: POST requests increase from around 1% to around 3%, indicating form/search engine abuse.
- Source profiles: There is an increase in traffic from infrastructure/cloud providers instead of distribution via end-customer ISPs.
- Geographical anomaly: A large proportion of Iranian requests originate from a single ISP almost entirely. It is unusual for one provider to account for 99% of a country’s internet traffic.
- No clear error waves: Moderate changes in the 500 and redirect rates indicate that there is no complete system failure.
Plausible explanations based on the data
The combination of many unique IP addresses and a relatively small increase in bandwidth is consistent with the hypothesis of a botnet primarily sending Spartan HTTP requests, such as search queries or form submissions.
Possible Variants:
- Compromised Servers/Cloud VMs: A volume of traffic from infrastructure providers indicates that there are many powerful servers, not just IoT devices, as sources. These hosts can generate numerous requests with minimal overhead.
- End-user bot activity in specific countries: Highly concentrated traffic from a single country may indicate targeted proxies or orchestrated action.
- Slow or “connection-heavy” attacks: Even if there are no classic Slowloris attacks, a similar effect can occur. Many simultaneous, short-lived connections can exhaust server resources. Modern browsers optimize connections using keep-alive, multiplexing, and session reuse. This results in less overhead per request. Simple bots, instead, establish a new TCP connection for each request. Each time, the server must perform the complete connection setup, including the handshake and TIME_WAIT phase.
The result is thousands of short-lived connections that transfer very little data but still consume significant resources.
Even a simple botnet can achieve the effect of a Slowloris attack simply through the sheer number of connections.
Why browsers and bots behave so differently
Real browsers are “cooperative.” They keep connections open, bundle requests, use HTTP/2 multiplexing, and efficiently process content. Bots, on the other hand, open many small sessions, often without keep-alive or compression, and only request bare HTML pages.
This results in a high volume of connections with low bandwidth and thus, which matches exactly what we see in the customer’s logs. It is of note that many of these bots do not retrieve images or scripts, nor do they interact with forms or cookies. This confirms that these are not real users but automated crawlers or attack scripts that systematically scan endpoints or perform stress tests.
What is missing so far and why it is important
Current monitoring data only provides a trend data. It lacks details about the behaviour of individual connections. For example, it is unclear whether the requests were short-lived or long-lasting, how much data was transferred per session, and whether the clients behaved like humans or machines.
Understanding this requires detailed network observation, i.e., collecting metrics that record individual sessions, request types, and response times. Additionally, short traffic recordings (packet captures) or higher-resolution flow data help identify patterns and repetitions.
Only then can one determine with certainty whether the activity is the result of coordinated bots, misconfigurations, or targeted stress tests. Bot management systems or web application firewalls (WAFs) could help, as they recognize bot behavior based on characteristics such as JavaScript activity, browser behaviour, and cookie usage.
This is essential to reliably distinguish human access from automated traffic.
Contact our experts and find out how you can remove harmful bots without blocking helpful bots. A proven Bot Management can help you with that.
Recommended immediate measures
The following pragmatic steps are recommended to stabilize the situation and gain insights:
- Bot Management and Web Application Firewall (WAF): Use a bot management tool or, as an interim solution, a WAF with rate limits and challenge mechanisms. CAPTCHAs for forms and JavaScript checks for search endpoints quickly reduce automated traffic.
- More detailed network monitoring: Activate session-based logs and packet captures to analyze individual request behaviour.
- Rate limits and rate-based rules: Enforce rate limits on search and contact endpoints, as well as connection timeouts and keep-alive limits.
- Provider contact: Identify Internet Service Providers (ISPs) that deliver unusually high amounts of traffic and submit abuse tickets.
- Content delivery and scrubbing: Determine if CDN or scrubbing services can absorb particularly active IPs or high-load sources (bots or servers) at short notice.
Why resilience must be learned now
This case represents a new hybrid bot phenomenon. It combines a high number of sources, low bandwidth per request and sustained stress on dynamic endpoints over a period of weeks. Classic threshold alarms are insufficient, and an adaptive monitoring and protection concept is required.
This incident demonstrates that network resilience is not achieved through rigid rules. It requires the ability to recognize behavioural patterns, trigger automated countermeasures and adapting to them dynamically.
Contact us if you want to understand how resilient your services are against such subtle bot activities. We support you with analysis and design of protection strategies, so your infrastructure remains stable even against quiet but persistent attacks.
A pattern appeared in the monitoring dashboard that indicated a classic DDoS attack. A trading platform was the target of massive web requests: there were two distinct traffic spikes in quick succession, both large enough to bring down an unprotected website. Let’s take a closer look at the larger of the two traffic spikes.
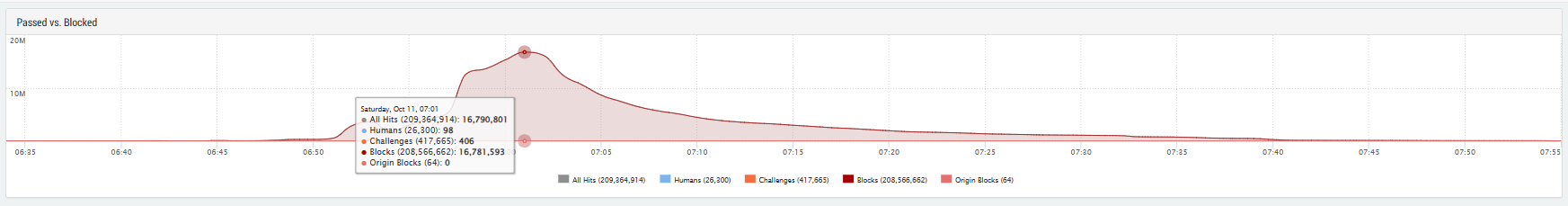
The measured peak values were around 16 million requests per minute with a bandwidth of 160 gigabits per minute, or about 21 Gbit/s. The requests were successfully repelled. However, the attack pattern reveals how sophisticated today’s botnets have now become and how seemingly minor details, such as the user agent, can play a highly crucial role.
No lightning attack, but a calculated ramp-up
The traffic did not surge at once and instead followed a characteristic curve. It rose slowly and steadily over several minutes. This controlled escalation is typical of attackers who first test their targets to ascertain whether a site is protected by mitigation systems.
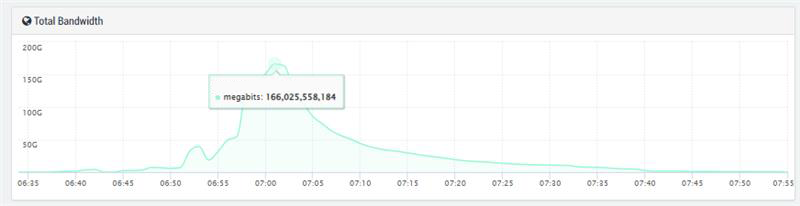
Such “soft” starts are more sophisticated than they appear: a sudden peak is noticeable, but a slow or gradual increase can trick those systems, which only respond to abrupt spikes in volume. The attack lasted less than half an hour.
A botnet that spans the globe
The source IP addresses were distributed across multiple continents including Indonesia, the US, China, Germany, India, Mexico, Brazil, Peru, and Russia. In total, more than 5,000 unique IPs were involved in the attack.
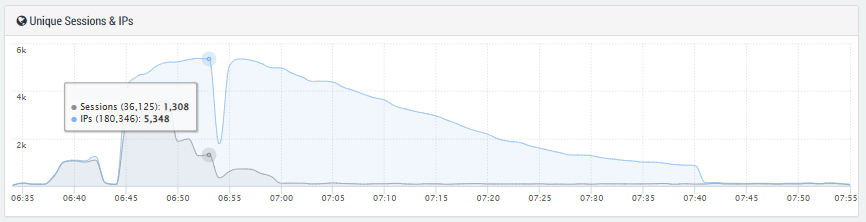
This broad spectrum suggests a large-scale, well-organized botnet. It was evident that cloud resources or powerful servers were used in several cases, as indicated by the high data throughput per host. It was particularly striking that a significant proportion of the requests came from the networks of large telecommunications providers. This suggests that compromised devices or servers within normal consumer networks were also involved. This is a classic feature of modern, “mixed” botnets.
Attack on the root domain
The attackers focused their attack on the entire website, i.e., the root domain, which is the home page and the central access point. The apparent aim was to make the entire website inaccessible.
The defense systems responded efficiently: Suspicious IPs were automatically moved to a quarantine zone and were blocked immediately, thus conserving resources and keeping the latency low. Most requests received an HTTP 403 response. This shows that the defense at the application level worked consistently and effectively.
When the user agent becomes a signature
One of the characteristics of this attack was the uniformity of the so-called user agents, i.e., the identifiers that browsers send to servers to identify themselves as “Chrome,” “Safari,” or “Firefox,” for example.
In this case, almost all requests used the same user agent string, a clear red flag.
- Real users use a wide variety of browsers, versions, and devices—in other words, many different user agents.
- If, on the other hand, thousands of IPs appear with the same user agent, this is an indication of automated requests, for example from a botnet or script.
- Modern protection systems recognize such patterns and block identical user agents when they come from many sources at the same time.
Disguised attacks vary user agents dynamically
Today, attackers can easily generate lists of thousands of realistic-looking user agent strings, many of which are publicly available. In an advanced version of the attack, each bot would use a different, plausible user agent string thus making it far harder to detect or block the traffic based on the signature.
In this case, however, stuck with two static user agents and thus failed at the first line of defense.
Why uniformity helps, but is also dangerous
For defenders, such uniformity is a stroke of luck. Simple rules such as “block all identical user agents with more than X requests per minute from different IPs” can work effectively.
But the threat landscape is rapidly evolving. Botnet frameworks are already in circulation that use randomized browser signatures, fake headers, or even simulated mouse movements to appear like real users.
This transforms the user agent from a simple identifying feature to one of the most important indicators of bot intelligence.
Learn more about a GDPR-compliant, cloudbased and patented DDoS Protection that delivers, what it promises.
Rebalancing during the attack
The traffic graphs revealed short pauses or drops in data volume. It is likely that the botnet was being restructured during these moments. The providers may have blocked suspicious IPs, devices may have lost connection, or the attackers may have switched to new address ranges.
This dynamic underscore the fact that this is a highly automated infrastructure. Botnet operators recognize in real time which parts have been blocked and automatically replace them with new resources. This requires technical control and resources. This was not the work of “script kiddies,” but rather a calculated, large-scale attack with global reach.
What can companies learn from this example?
This attack may seem less harmful compared to complex zero-day exploits, but it impressively demonstrates that even simple mechanisms – when scaled globally – can cause significant disruption.
For web platform operators, this means:
- Bot management is a must, not an option. Only those who intelligently detect automated access can separate legitimate users from malicious bots and protect system resources.
- User agent analyses provide valuable early warning signals. Uniform browser identifiers across many IPs almost always point to automation.
- Quarantine and rate limit rules prevent waste of resources. Suspicious IPs should be taken out of circulation at an early stage.
- Secure forensic data. Short packet captures and log excerpts help analyze patterns and trace attack paths.
- Keep an eye on cloud providers. Since many attacks exploit virtual machines in public clouds, targeted monitoring is critical for early detection of abuse.
The underestimated ally: the user agent
What began as a classic DDoS attack became a lesson in automation, reusability, and identity on the internet. The user agent, which is often overlooked or ignored, was the key to understanding and successfully defending against the attack in this case.
It showed that millions of requests were not genuine user activity, but rather coordinated actions of globally synchronized botnet. Modern internet security depends not only on bandwidth or hardware, but also on artificial intelligence, pattern recognition, and the continuous learning of defense systems.
Are your protection systems ready for the next wave?
We help companies reliably detect botnet traffic, refine user agent-based detection mechanisms, and develop flexible defense strategies.
Contact us for a no-obligation security analysis before the next spike hits.
Volumetric DDoS attacks typically follow a clear pattern: a brief buildup followed by a sudden peak, often within seconds. The target is flooded with traffic until the attackers exhaust their resources, or a mitigation system takes over. However, in the incident described below, a different scenario unfolded.
Over the course of several hours, one actor attacked three endpoints: two in the same subnet and one in a different infrastructure. Rather than following a simple “fire at will” pattern, the attacks came in waves of short, sometimes inconspicuous peaks, followed by longer phases of relative calm and renewed, stronger surges. The attacker’s staying power was particularly striking. While many campaigns fizzle out after a few minutes, this attack lasted from mid-morning until late afternoon.
Key features of the incident
The analysis revealed several notable data points. Firstly, the attack involved continuous activity for around five to six hours and targeted three endpoints synchronously. The tactic was revealed to be adaptive. Firstly, small test waves were sent out, followed by their gradual escalation. UDP floods dominated in terms of the protocol, alongside TCP/HTTPS via port 443. Peaks ranged from tens to several hundred gigabits per second. This approach indicates an attacker with significant resources and one who is likely controlled by a botnet with automatic scaling.
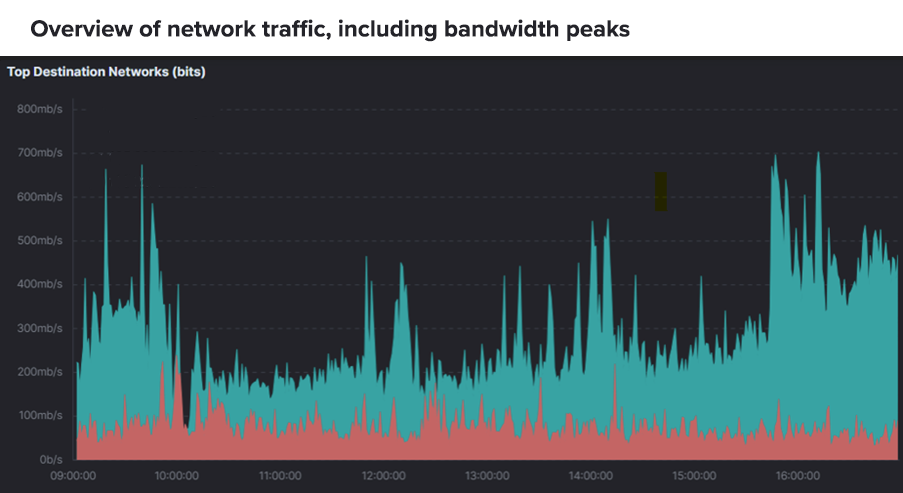
Dynamics of the attack waves
The first wave of attacks seemed harmless enough, with peaks of around four gigabits per second. However, the situation gradually escalated. Over the following hours, the waves grew larger and more unpredictable, posing a significant threat to many systems. There were often peaks between 20 and 70 gigabits with isolated incidences exceeding this range. After hours of seemingly routine waves, peaks in the range of several hundred gigabits to one terabit were recorded towards the end of the attack.
Unlike the steady increase and subsequent sustained load typical of ramp-up patterns, the attacker repeatedly allowed the targets to “catch their breath,” only to return abruptly. These pauses seemed almost like tests. The attacker verified resistance and then increased the strike rate.
Learn more about a GDPR-compliant, cloudbased and patented DDoS Protection that delivers, what it promises.
Technical anomalies in detail:
When defending against DDoS attacks, it is important to consider both the volume and the patterns. The following were particularly noticeable:
- Packet counts: The number of packets per second was exceptionally high. Even with ample bandwidth, firewalls and routers can collapse under this load.
- Protocol mix: A large proportion of the traffic consisted of classic UDP floods. At the same time, TCP streams were observed on port 443, indicating the misuse of proxies or the compromise of web servers.
- Package sizes: The distribution was unusually mixed. Rather than exclusively small fragments, packets of various sizes appeared, which indicated the use of different attack tools or botnet components.
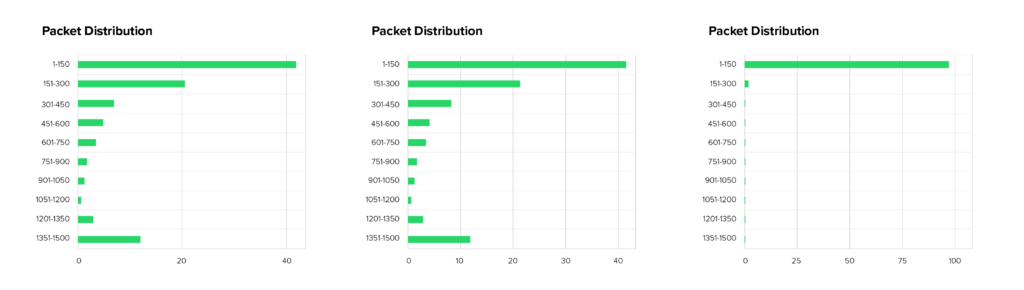
Origin and infrastructure used
The sources of the attack were widely scattered. Much of the traffic originated in China and India. Addresses from Europe also appeared, including those of well-known carriers and cloud providers. Notably, comparatively few IP addresses delivered large amounts of data. This suggests that powerful servers or compromised virtual machines, in addition to weak IoT devices, were also involved. Such “powerful bots” can generate tens of gigabits per second and quickly overwhelm traditional protection mechanisms.
Lessons for businesses
This attack demonstrates that DDoS actors do not rely solely on brute force; rather, they vary and test their methods over long periods of time. For businesses, this means their defence mechanisms must be flexible. It is also important to realize that defending against volumetric DDoS attacks is not a sprint but a marathon. This incident makes it clear that network resilience is not created by rigid walls, but by the ability to learn and adapt continuously – much like the attackers.
Would you like to know how prepared your company is for such attacks? Get in touch with us! We can help you analyse and develop customized defence strategies and practical plans.
The pro-Russian hacker group NoName057(16) is making headlines again. Between the end of July and the beginning of August 2025, the public websites of several German cities, including Trier, Mainz, Ludwigshafen, and Koblenz, were the target of coordinated DDoS attacks. These incidents highlight the growing threat posed by politically motivated cyberattacks in the context of hybrid warfare against states and municipalities.
International investigators strike against NoName057(16)
An entire infrastructure can be paralyzed with just one click. Between July 14 and 17, 2025, international investigators took action against the pro-Russian cybercrime network NoName057(16), which specializes in DDoS attacks. Under the code name “Operation Eastwood,” Europol coordinated an international strike involving authorities from over a dozen countries, including Germany, France, the US, and the Netherlands. The operation was also supported by ENISA and private partners.
The goal was to take NoName057(16)’s central server infrastructure offline, warn hundreds of supporters, and hold those behind the attacks accountable internationally. Investigators uncovered a network that is ideologically motivated but technically relatively simple, skillfully using gamification and cryptocurrencies to recruit volunteers. The attacks are specifically targeting countries that support Ukraine in its war against Russia. They show how political conflicts are increasingly shifting to the digital world.
Although “Operation Eastwood” was a severe blow to the hacker group, NoName057(16) reappeared shortly afterwards.
Return of the attacks: Trier and other cities affected
The first new attacks were documented on July 29, 2025, and intensified in the first week of August. The cyberattacks affected several websites of cities and districts in Saxony-Anhalt and Thuringia, including Magdeburg and Erfurt.
At the beginning of August, Mainz, Ludwigshafen, and Koblenz were also hit alongside Trier. According to the LKA, only public websites were affected; the city administration’s telephone and email communications remained fully functional. The financial damage was minor; the primary goal was to temporarily overload and disrupt the servers.
NoName057(16): Digital partisans in hybrid warfare
NoName057(16) is not just a group of hackers but acts as a digital paramilitary organization in hybrid warfare. Their actions illustrate how cyberattacks have become part of geopolitical conflicts – often below the threshold of conventional warfare.
For states, companies, and organizations in NATO countries, this means that the threat of ideologically motivated cyberattacks is real and requires long-term, continuous vigilance, strategic planning, and technical defenses.
The digital echo of war
Just a few days after Russia’s large-scale invasion of Ukraine in March 2022, the pro-Russian hacktivist network NoName057(16) became active. Since then, the politically motivated group has specialized in large-scale DDoS attacks targeting government and public institutions in countries that oppose Russia. According to the Insikt Group, the group recorded over 3,700 individual attack targets between July 2024 and July 2025, with Ukraine being the most affected, followed by France, Italy, and Sweden.
At its core, NoName057(16) operates for ideological reasons rather than financial gain. The network uses its own DDoS tool, “DDoSia,” which enables even technically inexperienced volunteers to carry out attacks. The group recruits helpers via Telegram channels, distributes attack targets, and rewards active participants with cryptocurrencies—a system that combines political loyalty and gamification.
Learn more about a GDPR-compliant, cloudbased and patented DDoS Protection that delivers, what it promises.
Technical structure and modus operandi
The infrastructure of NoName057(16) is remarkably structured. Tier 1 servers, which are only active for a short time, communicate exclusively with secure Tier 2 servers. This keeps control over the attacks stable. An analysis of the activities suggests that the operators work according to the Russian time zone and add new targets in two daily waves. This makes the attacks appear planned and coordinated.
The targets of the attacks are clear: disrupting critical government services, drawing public attention to pro-Russian narratives, and retaliating for political measures against Russia. Examples include attacks on Lithuanian infrastructure following EU sanctions, on Danish financial institutions for supporting Ukraine, and on Italian websites following “Russophobic” statements by the president.
Sisyphean task in the digital space
The fight against politically motivated and pro-Russian hacker groups such as “NoName057(16)” is like a modern-day Sisyphean task: with just one click, an entire infrastructure can be paralyzed, and every blow against the perpetrators is quickly answered with new attacks.
Although “Operation Eastwood” showed that international investigators can work together effectively to paralyze central structures and track down those behind them, the return of NoName057(16) just a few weeks later highlights the ongoing threat.
For states, municipalities, and companies, this means that cyber defense is not a one-time endeavor. Instead, a continuous and strategic approach is needed to remain capable of acting in a digital war.
Many people still think of DDoS attacks as pure volume battles, so when there is talk of terabit peaks, overloaded backbones, and massive bandwidth battles, they sit up and take notice. However, attacks can also take place in other dimensions, but the consequences can still be just as serious.
A recent example shows how precisely Layer 7 DDoS attacks (also known as application layer attacks) are orchestrated today. This was not a case of hours of continuous load or record volumes, but rather the targeted paralysis of a web application through massive parallel sessions.
Small but powerful
The attack began inconspicuously. There was no unusual increase in the backbone and no overload of the lines. It was only when the web servers were analyzed that it became clear something was wrong.
- Within a few minutes, around 580 million HTTP requests were fired at a single domain.
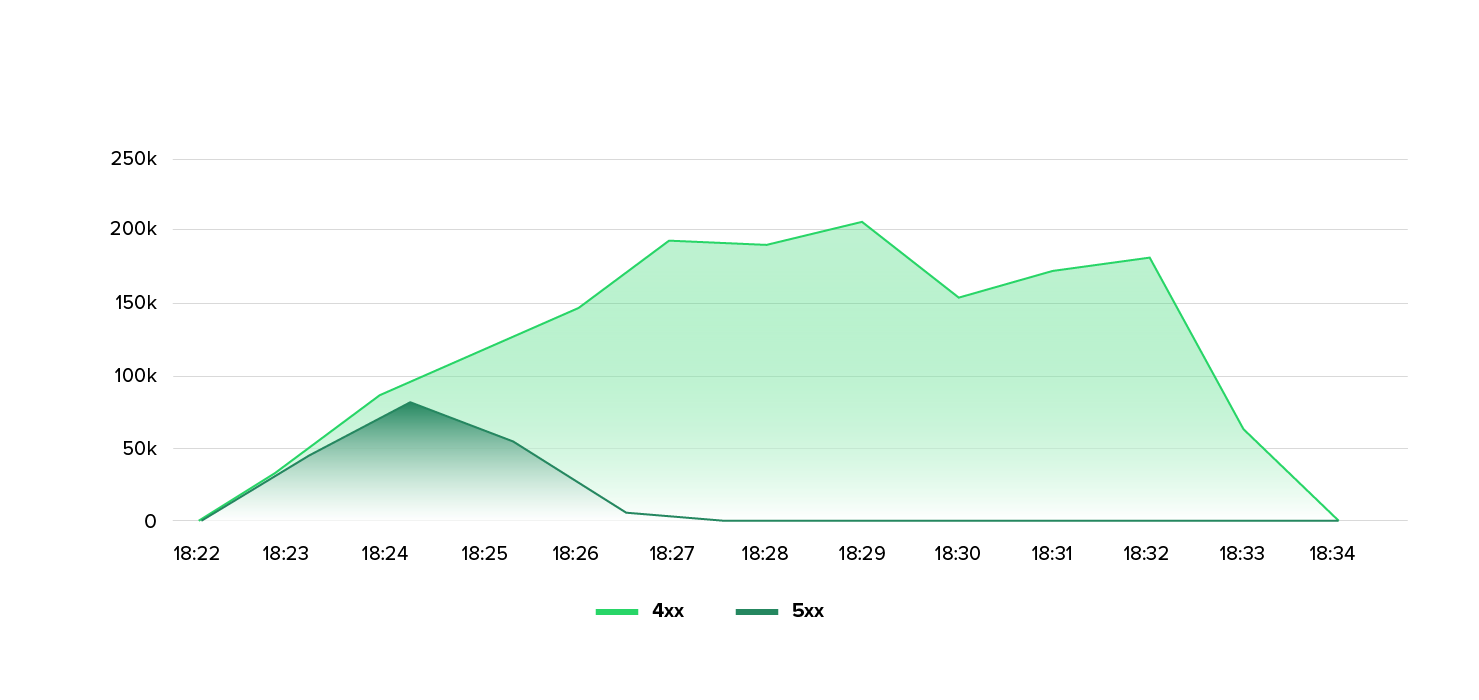
- At times, up to 16 million sessions were established in parallel per minute.
- Around 1,000 different IP addresses were involved, which together generated a highly distributed attack.
- The requests were standardized HTTP GET requests—simple, but overwhelming in their sheer volume.
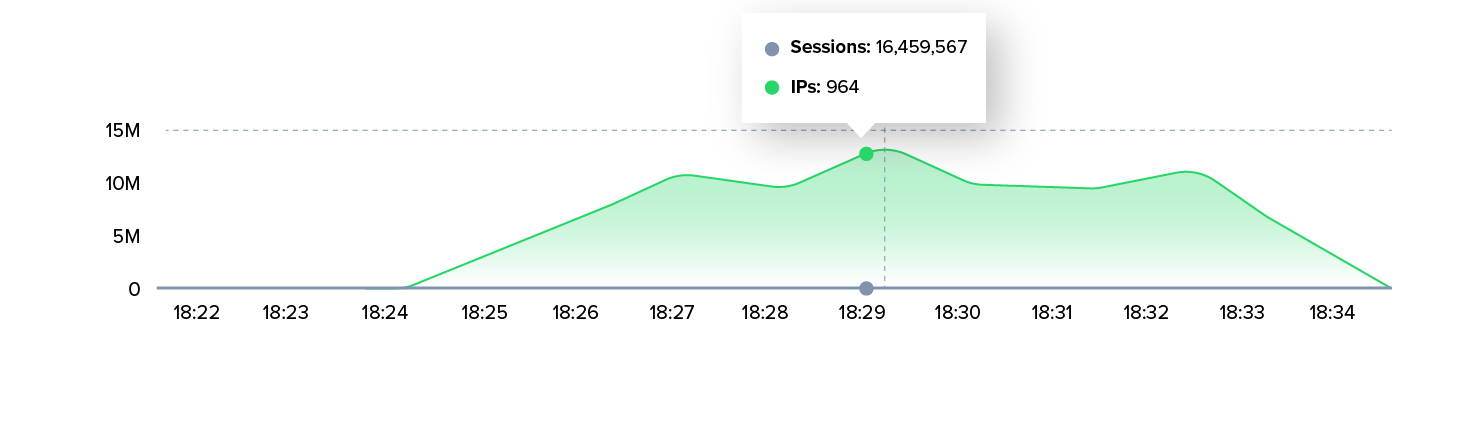
The result: The application came under massive pressure—not because of the bandwidth, but because of the overload of CPU, memory, and session handling.
How the attack worked
While volumetric attacks primarily “clog the pipes,” a Layer 7 attack targets the application layer. Here, it is sufficient to send millions of seemingly legitimate requests within a short period of time. Web servers have to process each of these requests and quickly reach their limits.
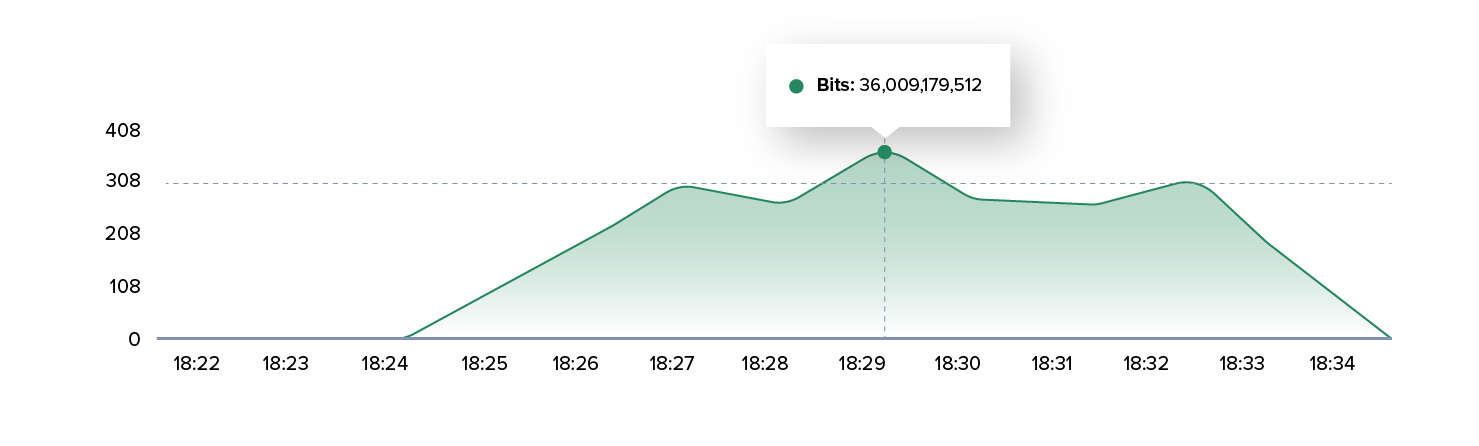
Particularly striking in this case was that:
- The attack was limited to the root domain, not to deeper directories or APIs.
- The requests themselves looked “normal” to outsiders. They were not exotic protocols or faulty requests, but regular GET calls.
- More than 102 million bot requests were detected and blocked.
This highlights the particular danger: such attacks are difficult to distinguish from regular user behavior.
Real-time defense
The response of the protection systems was crucial. The Web Application Firewall (WAF) detected anomalies early on. Several security rules were triggered simultaneously, such as:
- Unusually high request rates per IP
- Parallel sessions in unusual density
- Access patterns that did not correspond to human behavior
As soon as a source was classified as suspicious, an additional block was activated at Layer 3. This prevented further malicious traffic from this IP range from even reaching the application layer. In addition, the systems implemented a kind of “quarantine” in which attacker IP addresses classified as suspicious were automatically added to a block list.
The result: Although the attack was able to generate load in the short term, it was increasingly diverted into a dead end as it progressed.
A learning botnet
The adaptability of the botnet was particularly interesting. New IP addresses appeared continuously during the attack. As soon as one group was blocked, the next was reloaded. This behavior indicates automated control with a globally distributed infrastructure.
In other words, this was not a static botnet that would have fizzled out after a few minutes. Rather, it was a highly flexible attack tool that was able to respond to defensive measures.
Learn more about a GDPR-compliant, cloudbased and patented DDoS Protection that delivers, what it promises.
Why Layer 7 attacks are so dangerous
Volumetric attacks are usually easy to detect. Bandwidth explodes, routers and switches sound the alarm. Application layer attacks, on the other hand, often operate below this threshold. They exploit weaknesses in the application itself.
The main risks are:
- Deceptively real: The requests resemble normal user requests.
- Resource-intensive: Every single request takes up server capacity.
- Difficult to detect: Classic network filters often fail to catch them.
Companies that are heavily dependent on their web presence — such as those in the e-commerce, gaming, or digital platform sectors — are particularly at risk of even short attacks that lead to noticeable outages and lost revenue.
Lessons learned from the attack
This incident makes it clear that modern DDoS attackers do not necessarily have to rely on sheer size. Precision beats volume. With relatively few resources—in this case, fewer than 1,000 IP addresses—it’s possible to cause massive damage if the attack tactics are chosen wisely.
Key findings:
- Early anomaly detection is crucial for stopping Layer 7 attacks in time.
- Automated defense must be adaptive and able to adjust to changing patterns.
- Multi-layered defense — from the backbone to the application — is necessary to close gaps.
Conclusion
DDoS attacks have long been more than just a race for the highest bandwidth. Today, the danger lies primarily in the combination of technical sophistication and targeted attacks on applications. A Layer 7 attack has shown how serious even “invisible” attacks can be when millions of sessions are established within minutes without any regular user purpose.
Anyone who wants to protect their services must think defensively in depth: not only fending off gigabit attacks, but also understanding patterns, analyzing behavior, and responding flexibly. This is the only way to effectively defend against highly sophisticated attacks such as these.
Within the space of a few days, Link11 observed a wave of DDoS attacks that stood out – not for their duration or scale, but for their surgical precision. A company in the digital entertainment sector was attacked nine times. Rather than relying on prolonged overload, the attackers opted for a “hit-and-run” strategy: short bursts of traffic, each lasting only 5-10 minutes, but reaching peak loads of up to 1 Tbit/s. The attacks were distributed over six days and consistently targeted two specific IP addresses – at different times and with high throughput.
What made this campaign remarkable wasn’t just the raw traffic volume, but the method, which was brief, focused, and effective. The limited duration of each attack made analysis challenging, while still revealing clear strategic intent.
The attacks had three key characteristics:
Short but intense:
Each DDoS attack lasted only a few minutes yet unleashed massive data streams ranging from gigabit to terabit levels. The cumulative traffic volume spanned several hundred terabytes, with spikes up to one trillion bits per second (Tbit/s), compressed into narrow time windows.
Recurring and staggered:
Rather than sustained pressure, the attacks occurred multiple times per day at different times. The rapid surge in traffic – from zero to several hundred Gbit/s within seconds (“fast ramping”) – left little time for traditional mitigation strategies to respond, allowing for maximizing disruption with minimal exposure.
Technically varied, strategically controlled:
Initially, the attackers used UDP floods on port 443 to disrupt encrypted traffic (QUIC/HTTPS). Over time, the tactics shifted:
- Initially, UDP floods were used on port 443 to specifically disrupt encrypted web communication (QUIC/HTTPS).
- Follow-up attacks added TCP 80 floods to maintain high bandwidth.
- Later waves introduced variable-size packets on TCP ports 80 and 443 with a lower volume (~200 Gbit/s) but more complex behavior.
- One wave targeted UDP 123 (NTP), a rarely used protocol often seen in reflection attacks. This traffic was limited to 40 Gbit/s and consisted of small packets and random target ports.
- The campaign concluded with a return to the initial pattern of high-bandwidth floods on UDP and TCP 443 using large packets, varied source ports, and IP addresses.
Packet analysis revealed a strategic evolution: the initial waves featured consistent packet sizes, which is typical of reflective attacks, while later stages showed mixed packet sizes, likely to bypass signature-based defenses.
The distributed origin of the traffic, spanning various source autonomous system numbers (ASNs) and entering through all major Link11 nodes, indicates a high level of load balancing and possibly spoofed or compromised IP addresses. This makes attribution difficult and suggests a large, globally dispersed botnet.
Informed and deliberate targeting
Traffic patterns strongly suggest that the attacker had prior knowledge of the target’s infrastructure, especially its HTTPS services. The timing of the attack, the protocol selected, and the specificity of the target point to a deliberate effort to disrupt key digital services with minimal noise.
The overall strategy suggests:
- The attacker understood the architecture and services in use.
- Attack windows and protocol choices were optimized for disruption and efficiency.
- A global botnet infrastructure enabled wide distribution across multiple carriers, possibly to exploit regional weaknesses or saturate key transit nodes.
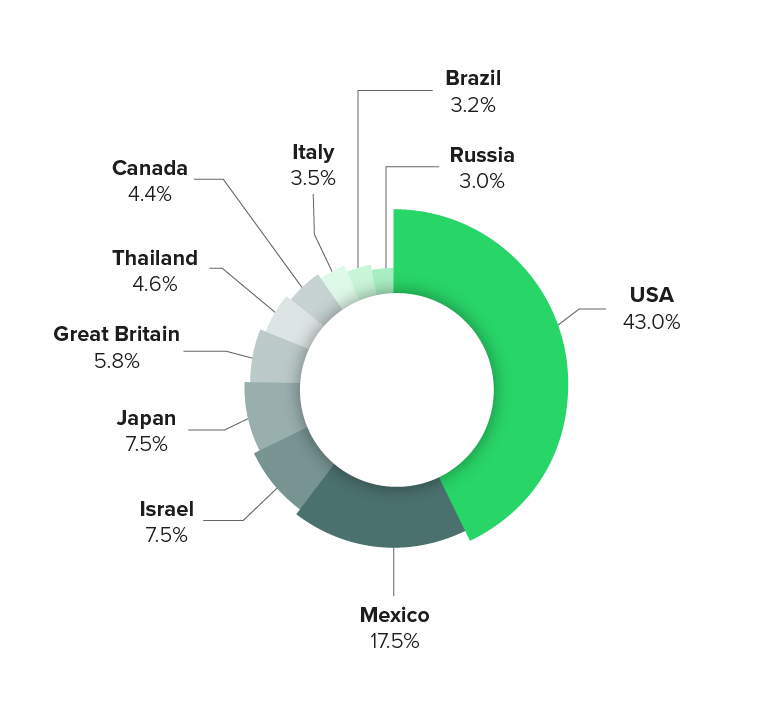
Likely motivation: Competition, not geopolitics
Given the target’s position in the digital entertainment sector, which is frequently hit by financially motivated cyberattacks, it is plausible that the attacker’s goal was commercial disruption. Attack timing that aligns with peak usage further supports this theory.
Additional insights:
Beyond the immediate impact, the campaign reveals important trends in modern DDoS behavior:
- Botnet preparation: In the days leading up to the main wave, smaller probing patterns were observed – likely reconnaissance or test phases.
- Adaptive tactics: Protocols and source behavior shifted between attacks, suggesting that the attacker adjusted in response to mitigation attempts.
- Operational efficiency: The use of short bursts and freely accessible tools (e.g., open proxies, spoofing, and low-cost botnets) indicates a cost-effective attack model with a low barrier to entry.
Learn more about a GDPR-compliant, cloudbased and patented DDoS Protection that delivers, what it promises.
Implications for Defense
Such attacks are difficult to detect and even more difficult to defend against. Their brevity complicates forensic tracing, and their variability poses a challenge to automated filters. For attackers, their effectiveness is undeniable.
Robust defenses should include:
- Dynamic detection that analyzes not only volume, but also packet behavior and timing.
- Behavioral analysis at both the network and application layers.
- Geographical and systemic redundancy in mitigation infrastructure.
- Preparedness for specific DDoS patterns (e.g., UDP 443 floods, TCP reflection) supported by tailored incident response playbooks.
Conclusion: Precision is the new threat dimension
This campaign underscores a growing shift in DDoS strategy. Attackers no longer need overwhelming force; intelligent timing, protocol agility, and infrastructure knowledge are sufficient to cause significant disruption.
Effective defense requires more than just bandwidth. It demands intelligent, adaptive systems that can analyze traffic and recognize behavior in real time – before service interruptions occur.
Would you like to know how your company is equipped to defend against tactically sophisticated DDoS attacks? Our experts will support you in analyzing, planning, and implementing effective protection solutions.
During the NATO summit, 27,000 police officers physically protected The Hague, but they were powerless against digital attacks. What is currently happening in the Netherlands is a prime example of a new era of politically motivated cyberattacks that systematically threaten democratic processes.
NATO summit as the perfect backdrop for cyber warfare
While the heads of state and government of 45 countries gathered in The Hague for the NATO summit, the pro-Russian hacker group NoName057(16) used the major political event as motivation for a coordinated cyber offensive. The attackers specifically targeted the NATO Regional Representation in the Netherlands and several municipalities and provinces, including Den Bosch, Delft, and The Hague.
The attack on NotuBiz, an IT service provider for municipalities and political institutions, temporarily rendered important documents inaccessible. As a result of the attack, various domains used by the municipality of The Hague were temporarily restricted or unavailable.
Systematic waves of attacks in the Netherlands
In 2024 and 2025, the Netherlands was the scene of an unprecedented series of politically motivated cyberattacks that revealed a clear pattern of state-sponsored digital retaliation.
EU elections as the first target
Back in June 2024, the pro-Russian hacker group HackNeT used the EU parliamentary elections to launch a coordinated cyber offensive against Dutch political party websites. The documented figures reveal the massive scale of these attacks: over 1 billion HTTP requests had to be fended off every day, with individual websites being bombarded with up to 115 million requests per hour.
The four-hour waves of attacks on June 5 and 6 demonstrated for the first time the full potential of large-scale botnet infrastructures against democratic processes.
Education sector under constant attack
In January 2025, the situation escalated dramatically when DDoS attacks paralyzed the Dutch education sector. SURF, the IT organization for universities, reported massive disruptions caused by a DDoS attack that brought the universities’ shared network to a standstill.
Maastricht University reported campus WiFi and VPN services down, while Tilburg and Utrecht were also severely affected. At the same time, the DigiD system was attacked – Logius, the government agency responsible for digital identities, confirmed the attack and attributed the outages to the sheer volume of traffic, which overwhelmed the system’s defenses.
Retaliation for aid to Ukraine
The political motivation became unmistakably clear in April 2025, when NoName057(16) systematically attacked Dutch provinces. The hacker group explicitly justified its attacks with the Netherlands’ aid to Ukraine: The Netherlands had sent €6 billion in military aid to Ukraine in February and allocated a further €3.5 billion for 2026.
According to NoName057(16), this meant that the authorities had to cut the budget for education and research by €1.2 billion. The attacks specifically targeted the provinces of Drenthe, Groningen, North Brabant, North Holland, and Overijssel, as well as cities such as Gouda, Tilburg, Almere, Breda, Apeldoorn, Haarlemmermeer, and Enschede.
NATO summit as the climax
The series of attacks reached its preliminary climax during the NATO summit in The Hague, when NoName057(16) targeted the NATO Regional Representation and strategically important municipalities. The attack temporarily rendered important government documents inaccessible and demonstrated the vulnerability of democratic infrastructures.
These waves of attacks reveal a new quality of hybrid warfare: every geopolitical event is systematically exploited for cyberattacks to disrupt democratic processes and exert political pressure.
BKA situation report confirms dramatic trend
The latest figures from the BKA’s 2024 cybercrime situation (German Police Agency) report confirm a worrying development: hacktivist DDoS attacks are rapidly increasing and cybercriminals are increasingly targeting the websites of public administrations and authorities.
Dramatic damage figures
- €178.6 billion in damage caused by cyberattacks in Germany
- Three quarters of all damage is caused by cyberattacks
- 201,877 cybercrime offenses committed abroad – 31.4% of all offenses committed abroad are cybercrime offenses
- Clearance rate only 32% for cybercrime offenses
Germany already in the crosshairs
The BKA documents specific attacks and reports that the websites of the state government, the state police, and the state office for the protection of the constitution of Mecklenburg-Western Pomerania were only partially accessible for several hours due to DDoS attacks. The pro-Russian hacktivist group NoName057(16) claimed responsibility for the attacks via Telegram.
Digitalization of geopolitical conflicts
A key finding of the BKA’s assessment is the increasing spread of geopolitical conflicts into the digital space. The perpetrators can be divided into two main camps: pro-Russian or anti-Israeli, with their motivation stemming from geopolitical conflicts that have been increasingly transferred to the digital space since 2022.
Technical realities: simple but effective
Low barriers to entry
The Dutch IBD (“Informatiebeveiligingsdienst,” or “Information Security Service”) notes that DDoS attacks are relatively easy to carry out due to readily available tools and therefore do not require much technical expertise. The consequences remain limited, as the underlying systems are not affected.
Focus on symbolic effect
According to the IBD, the impact of DDoS attacks is often limited and symbolic. Groups behind DDoS attacks use strong rhetoric to generate attention for their digital attack and political goals, often spreading it via social media.
Massive infrastructure required
The documented attacks are only possible through botnets with tens of thousands of coordinated devices, similar to the networks that were dismantled in Europol’s Operation Endgame.
Learn more about a GDPR-compliant, cloudbased and patented DDoS Protection that delivers, what it promises.
BKA warns of AI-assisted cyber attacks
The federal situation report predicts a further escalation of the threat situation as artificial intelligence is increasingly used for cybercriminal activities. The BKA expects AI-supported crimes to become even more prevalent in the future. AI can not only make cyberattacks more professional, but also enable them to reach a wider scope and higher level of criticality through automation.
What democratic states must do now
In light of the escalating DDoS threat, as currently observed in the Netherlands, organizations must fundamentally rethink their cyber defense. Analysis of the systematic waves of attacks reveals specific requirements for effective protection:
- DDoS protection solutions: Professional mitigation services are essential for robust protection of digital infrastructure
- Redundant systems: Multi-layered firewall architectures have proven effective in traffic filtering
- Monitoring: Early detection of anomalous traffic patterns for timely response
Conclusion
The systematic attacks on the Netherlands reveal a new quality of hybrid threats, one that is no longer purely theoretical. Politically motivated DDoS attacks have become the digital weapon of choice for state-sponsored or ideologically motivated actors.
Link11 is ready when the next attack strikes. Because one thing is certain: the question is not if, but when the next attack will come.
End of April 2025: While the political debate in Germany is coming to a head over the planned delivery of Taurus cruise missiles to Ukraine, a digital offensive has begun in its shadow. Pro-Russian hacker groups – led by NoName057(16) – are intensifying their attacks on German companies, institutions, and cities.
Within a few days, websites of state banks, industrial companies, and city administrations are paralyzed by targeted DDoS attacks. NoName claimed responsibility for the attacks via Telegram, marking a new level in geopolitically motivated cyber warfare against German targets.
While portals such as berlin.de, stuttgart.de, and nuernberg.de were unavailable for hours or even days, simultaneous attack attempts were recorded on company websites such as Volkswagen, Lidl, and Commerzbank.
We observed a Layer 7 DDoS attack on the Link11 network amidst this flurry of attacks that stood out not for its volume, but for its sophistication. There was no brute force data stream and no millions of packets per second, but rather a precise attack.
What is a Layer 7 DDoS attack?
A Layer 7 DDoS attack targets the top layer of network communication, the application layer. Typical forms of attack include sending massive numbers of HTTP requests to web servers or APIs in order to exhaust backend resources.
Unlike volumetric attacks, the strength of these attacks lies not in their bandwidth, but rather in the large number of intelligent, legitimate HTTP requests. These are difficult to distinguish from regular traffic.
Camouflaging with structure
At first glance, the attack appeared unremarkable: no unusual volume, no exotic countries of origin. What made it noteworthy, however, was the targeted use of well-known hosting providers whose infrastructure is also used by many VPN services.
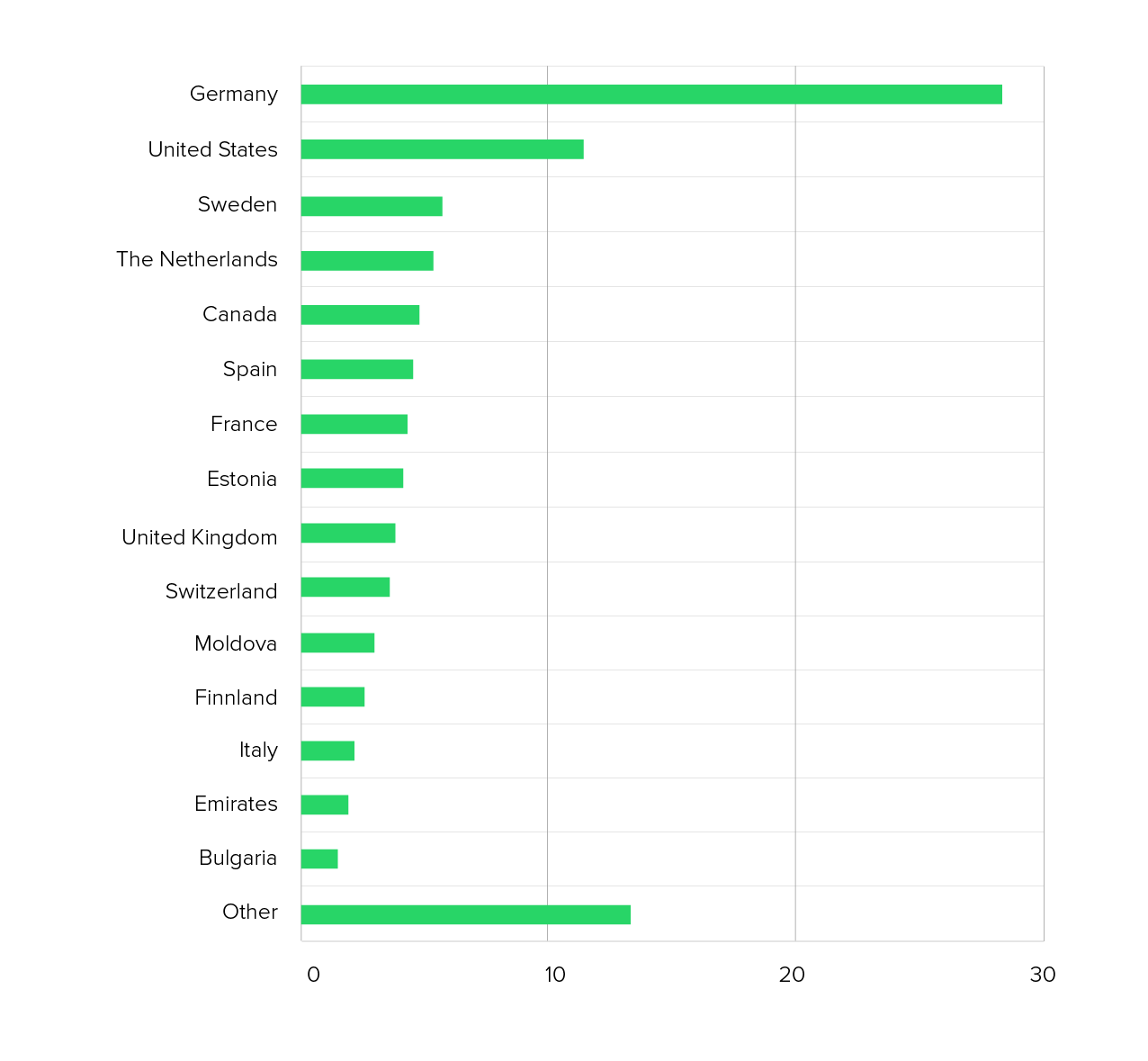
The most important features:
- IP ranges from Datacamp Limited and M247 Ltd.
- These providers are frequent hubs for VPNs such as NordVPN and ProtonVPN, as well as for CDNs such as CDN77.
- The HTTP requests were evenly distributed, structured, and designed for long-term use rather than overload.
This approach made immediate detection difficult, especially since the attack traffic was virtually indistinguishable from legitimate traffic.
The perfect mask
A key component of the attack was the consistent use of obfuscating infrastructure. Instead of relying on open bots or conspicuous proxy servers, the attackers routed their requests through networks that are normally used for performance optimization and data protection.
Tactics used for concealment:
- VPN and CDN tunneling: The attacks were routed through services that specifically enable Geo-IP obfuscation.
- Geotricks via edge nodes: Despite globally distributed source systems, many requests appeared to originate from Germany because they were routed through nearby CDN nodes.
This technical game of hide-and-seek made it nearly impossible to trace the actual sources of the attacks.
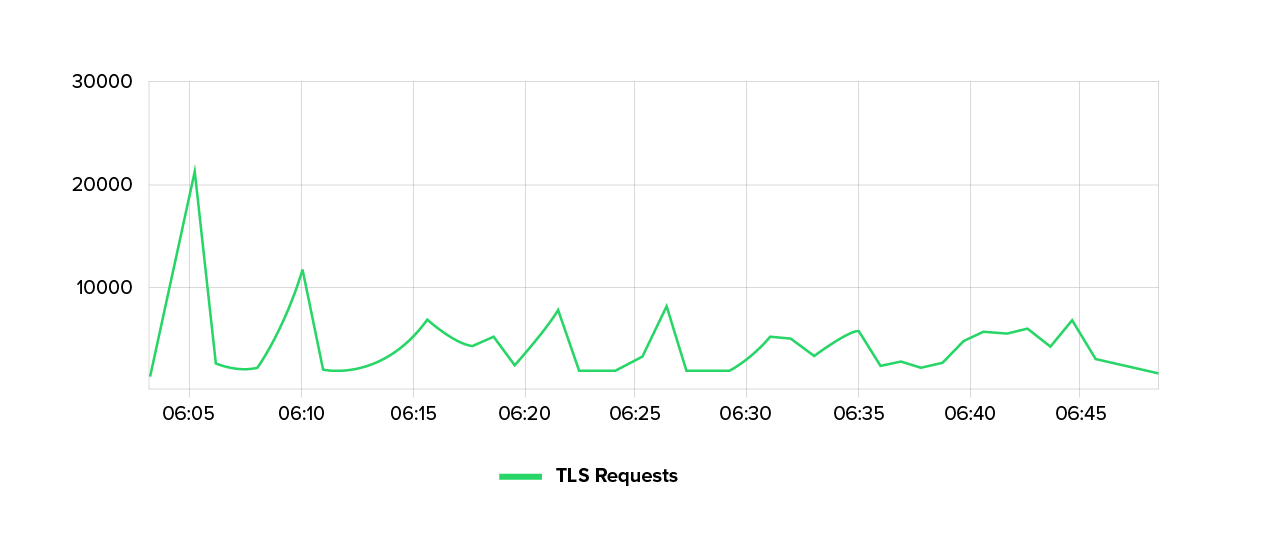
No storm, just pinpricks
The Layer 7 DDoS attack we investigated did not rely on massive amounts of data, but on targeted, tactically placed disruptions. At its peak, we recorded around 20,000 requests per minute. While this is not enough to immediately paralyze large systems, it is enough to have an impact on sensitive areas.
When machines fail because they want to appear human
A particularly interesting aspect was the way in which the protection solution detected and partially blocked the attack. The attackers had apparently tried to simulate human behavior, but they did not succeed completely.
The most common reasons for blocking were:
- Unusual HTTP header combinations (e.g., missing referrers, inconsistent user agents).
- Suspicious visitor profiles that did not “stabilize” via cookies or JavaScript challenges.
- Failed interactions with CAPTCHA or JS fallbacks, indicating simple bots.
Although the attack was technically sophisticated, it failed due to the lack of complexity of human browsing patterns – a good sign for modern protection solutions.
Learn more about a GDPR-compliant, cloudbased and patented DDoS Protection that delivers, what it promises.
DDoS for the small budget
The economic efficiency of this attack was also remarkable. The technical effort was low, but the impact was nevertheless measurable. Especially when compared to the parallel large-scale attacks on municipal portals, a possible pattern emerges here: the targeted use of limited resources to disrupt digital processes.
Economic aspects at a glance:
- Low entry costs: VPN access usually costs only a few dollars, and in some cases is available for free via trial accounts.
- Microjobs for routine tasks: The mass creation of accounts or the rental of test servers can be outsourced for pennies.
- “Gold farming” logic: As in online games, monotonous tasks could be carried out in low-wage countries to build up attack infrastructure.
This development makes it clear that DDoS is no longer just a question of financial resources, but also of organization and intelligence in its construction.
Conclusion
The attack was designed less for brute force than for precision and concealment. Whether it was carried out by an inexperienced actor with limited resources or a larger group in the testing phase remains unclear.
One thing is certain, however: the ability to conceal the source of an attack makes it much more difficult to trace. This kind of DDoS attack is therefore a dangerous weapon in the arsenal of modern attackers.
Against the backdrop of the recent wave of attacks on municipal websites, it is clear that such Layer 7 techniques are not just isolated incidents, but are apparently becoming part of a strategic escalation against government and public IT infrastructures.
Covert, precise, difficult to detect – Layer 7 DDoS attacks require automated, intelligent protection strategies. Talk to our experts and we will advise you personally.
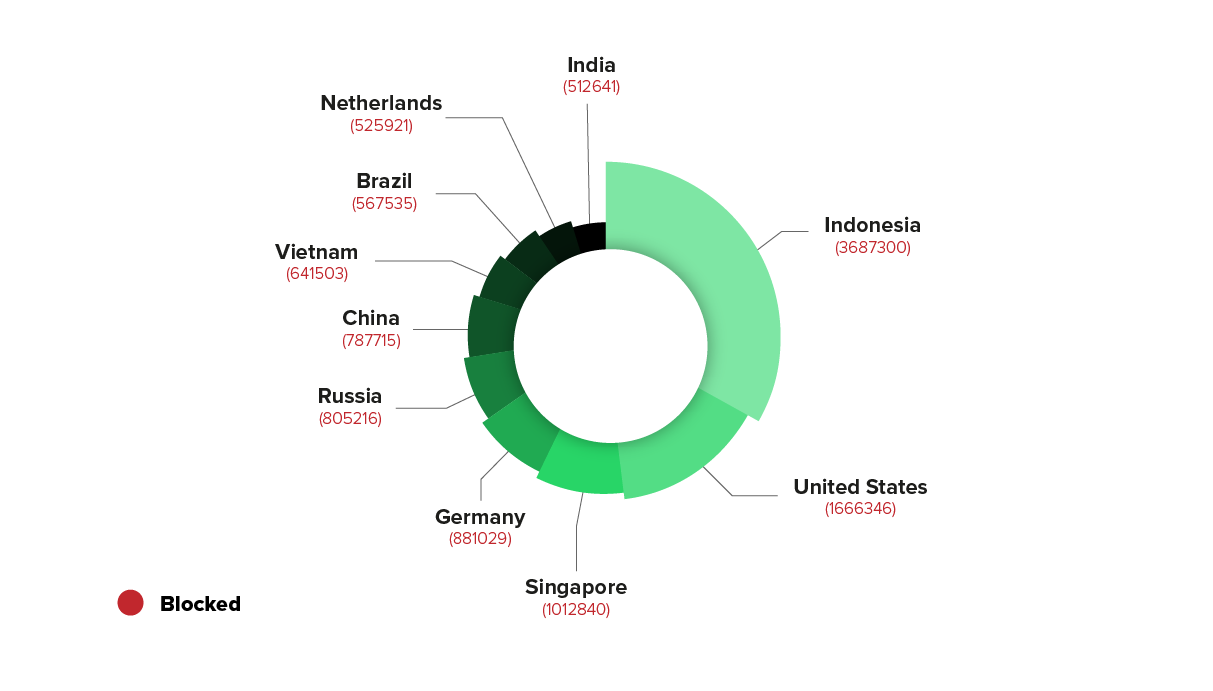
Recently, the website of an Israeli city administration experienced a brief but intense Layer 7 DDoS attack. The attack resulted in a flood of approximately 18 million HTTP requests, averaging over one million per minute. The attackers targeted only the root domain of the city’s website, leaving APIs and other endpoints unaffected.
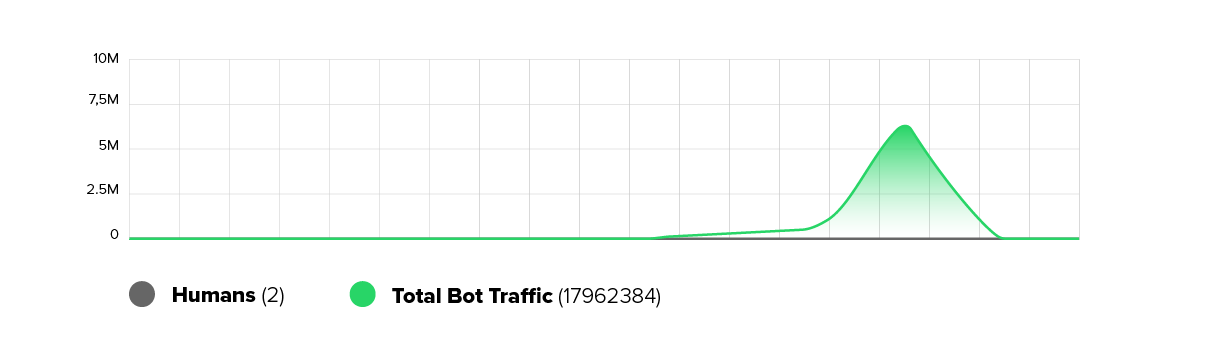
Technical Analysis of the Incident
The requests were generated by a globally distributed botnet with IP addresses from various countries, including Germany, Russia, and Ukraine. The nature of the attack suggests a classic Layer 7 DDoS scenario, which aims to overwhelm web applications by flooding them with a large volume of seemingly legitimate HTTP requests. The distribution across different IPs and countries indicates a botnet structure with globally distributed nodes.
Layer 7 attack pattern (HTTP flood)
Since only HTTP requests were directed at the root endpoint and other APIs remained unaffected, this indicates an HTTP flood attack at the application level (Layer 7). These attacks are more difficult to block than volumetric attacks (Layer 3/4) because they mimic legitimate traffic. No complex attack techniques such as low-and-slow or dynamic header variations were observed, suggesting standardized, generic bot traffic.
Mitigation Measures in Place
Thanks to a prepared architecture with load balancing, web application firewall (WAF) and automatic scaling, the affected platform was able to react quickly to the unusual load. The most important components at a glance:
- Dynamic scaling via Kubernetes
The application runs on a Kubernetes cluster with horizontal pod autoscaling. As the load increased, additional reverse proxy instances were automatically deployed. This rapid scaling ensured that neither the CPU nor memory resources became bottlenecks.
- Web Application Firewall (WAF) with Rate Limiting
A centralized WAF instance within the multi-tenant cluster continuously monitors traffic patterns. During the attack, the WAF automatically enforced a rate limit of 60 requests per minute per IP address. If that threshold was exceeded, the system triggered Rate Limit block and requests will be blocked.
- Web Application Firewall (WAF) with Dynamic Rule Limiting
Dynamic rule count blocked request and if detect a lot of blocked requests from single IP it was moved to a quarantine state. In this state, all subsequent requests from those IP addresses were ignored at the application level, which significantly reduced unnecessary load on backend services.
The technical defense delivered a clear result:
- Out of 18 million requests, around 17.7 million were automatically blocked or rejected. This corresponds to a success rate of more than 99%.
- System availability: The website remained available without interruption throughout the incident. Users did not notice any delays or outages.
- Resource utilization: Neither CPU nor RAM of the cluster nodes were pushed to their limits. The automatic scaling responded reliably and precisely.
Learn more about a GDPR-compliant, cloudbased and patented DDoS Protection that delivers, what it promises.
Lessons Learned and Recommendations
The successful mitigation of this attack underscores the importance of layered security strategies.
- Proactive scaling: Use infrastructure that can scale dynamically under stress.
- Intelligent Filtering: Implement behavioral detection mechanisms and adaptive rate limiting.
- Dynamic bot detection: Static block lists are insufficient against globally distributed botnets. Instead, analyze anomalies in request behavior in real time and enforce appropriate rules automatically. Tools such as JavaScript challenges or CAPTCHA alternatives are often effective.
- Challenge-response mechanisms: Incorporate unobtrusive methods, such as JavaScript challenges, to differentiate bots from human users.
- Segmentation: Ensure a clear separation between the different parts of your application (e.g., APIs and public web pages) to localize potential attack vectors.
Conclusion
In summary, although the DDoS attack was significant in terms of volume and geographic spread, the combination of automated defences and modern cloud infrastructure ensured a fast, transparent, and effective response that did not impact user experience or operational continuity.
Even publicly accessible platforms with relatively small data sets can be targets of automated mass attacks. Resilient infrastructure combined with intelligent traffic analysis and a timely response protects not only availability, but also citizens’ trust in digital government services.
Fortunately, with the right setup, most of these attacks can be fended off completely automatically, with no impact on users or the operations team.