Ask 10 security professionals the above question and you’ll get 12 different answers. Each of those answers is right for some organization but what is right for you, for your organization is dependant on how much risk you are willing to carry. The right amount of protection will balance the amount of Risk your organization is willing to carry, and that is an answer that has to come from within your organization, and from the management team, not the IT, Operations, or Security teams.
By instituting Risk Management policies you will have an evolving and comprehensive analysis of the strengths and weaknesses of your organizations security posture and where your vulnerabilities are in the current threat landscape. With a Risk Management Program, you can instead ask “What protection do I need to protect these systems from those threats?” which will have much more consistent answers.
Creating a Risk Management Program
A Risk Management program, while influencing and ultimately implemented by Information Technology, is in fact a management policy. As a policy it is prudent to define the program in terms of objectives, strategy, and objectives and refrain from requiring specific technologies, methodologies or implementations. By divesting objective from implementation you will create a much more flexible program that is able to quickly adapt to emerging technologies and threats. After all, it will almost always be faster to roll out a new technology than change a business policy AND roll out a new technology.
Executive Summary
The Executive Summary exists so that readers can, at a glance, determine if and why the policies applies in a given situation. It should be concise and cover three main points. Why the program is required, what organizational units are subject to the program, and what the desired outcomes from a successful program should be. These three points are generally referred to as the Purpose, Scope and Key Goals.
- Purpose: Define the purpose of the cybersecurity risk management program, including its importance in protecting the organization’s assets, reputation, and operational integrity.
- Scope: Outline the scope of the program (e.g., all internal networks, applications, cloud infrastructure, employee endpoints).
- Key Goals: Ensure business continuity, protect sensitive data, manage compliance requirements, and mitigate risks from both internal and external threats.
Governance and Leadership
As previously stated the Risk Management Program is foremost a matter of policy over implementation, as such a successful Risk Management Program needs to be driven by leadership. The Policy should outline specific roles and responsibilities for: the creation and maintenance of the policies, implementation, and periodic review of the program. At this level specific procedures should be referred at a high level and as external documents to maintain the separation between policy and implementation and, just like with specific technology, to preserve as much flexibility for updating and improving procedures.
- Cybersecurity Leadership: Establish roles such as Chief Information Security Officer (CISO) or cybersecurity director to lead the risk management initiative.
- Risk Management Committee: Set up a cross-departmental team (IT, legal, operations, and risk) to oversee the implementation of the cybersecurity strategy.
- Policies and Procedures: Develop cybersecurity policies, including incident response plans, data protection protocols, and user access control.
Risk Assessment and Threat Identification
After defining “Why” and “Who” the next section of the Risk Management Policy should define “What” is to be protected from “Which” threats. These questions are sometimes referred to as an Asset and Threat inventories. Your asset inventory can include hardware, software, processes even personnel that is critical to the successful operation of the organization. As above the specifics of this list should exist in separate documents, the policy should define the purpose for, scope of, and required information within each of these inventories.
- Asset Identification: Create an inventory of critical assets (data, systems, applications, and infrastructure).
- Threat Landscape: Identify common cybersecurity threats, such as:
- DDoS Attacks: Distributed Denial-of-Service, which targets network availability.
- Malware: Viruses, ransomware, Trojans, and spyware.
- Phishing and Social Engineering: Attempts to trick employees into disclosing sensitive information.
- Insider Threats: Risks from employees or contractors who intentionally or unintentionally expose data.
- Advanced Persistent Threats (APTs): Prolonged, targeted attacks aimed at stealing intellectual property or other high-value data.
- Data Breaches: Unauthorized access to personal or sensitive data.
- Vulnerabilities in Software/Hardware: Known vulnerabilities in applications, operating systems, or IoT devices.
- Threat Modelling: Use tools like the MITRE ATT&CK framework to categorize and model various attack techniques.
Risk Analysis and Evaluation
With the asset and threat inventories defined above you will need to conduct periodic Risk analysis. This is not a one-time task, and the execution of the Risk analysis will be result in documents external to the Risk management Policy. Within the Policy you should clearly articulate the frequency of these analyses as well as a consistent analysis framework.
- Likelihood and Impact Assessment:
- Likelihood: Assess the probability of different threats occurring (low, medium, high).
- Impact: Evaluate the potential impact on the organization (financial loss, reputational damage, operational disruption).
- Risk Matrix: Create a risk matrix that categorizes threats based on likelihood and impact, helping prioritize which risks require more immediate attention.
Furthermore you will want to establish procedures for periodic proactive assessment of your security posture for continuous improvement, and to discover potential vulnerabilities before they are exploited.
- Vulnerability Assessment: Conduct regular vulnerability scanning and penetration testing to identify gaps in defenses.
Contact our experts and find out how your business can be protected with an automated security solution.
Risk Mitigation Strategies
Which specific Threats need mitigation strategies is likely going to be a natural byproduct of both the above risk analysis and any applicable regulatory requirements (PCI-DSS, GDPR etc) at a minimum you will probably want to include a requirement for the organization to maintain up-to-date strategies for the following:
- DDoS Protection:
- Implement traffic filtering and rate-limiting to block malicious traffic.
- Use a Content Delivery Network (CDN) or acloud-based DDoS protection.
- Set up an incident response plan specifically for DDoS attacks, including communication protocols and escalation procedures.
- Endpoint Security:
- Deploy endpoint protection platforms (EPP) to safeguard devices from malware and viruses.
- Regular patching and updates to fix known software vulnerabilities.
- Network Security:
- Use firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS).
- Implement secure virtual private networks (VPNs) for remote access.
- Segregate sensitive systems using network segmentation to limit the impact of attacks.
- Email Security:
- Implement spam filters, email authentication (DMARC, SPF, DKIM), and educate employees on phishing risks.
- Use multi-factor authentication (MFA) for email and critical applications.
- Access Management:
- Use role-based access control (RBAC) to limit data access to authorized personnel.
- Regularly review access rights and remove inactive users promptly.
- Enforce MFA for critical systems and data.
Incident Response and Recovery
Moreso than any other document that results from the Risk Management Program, an Incident Response Plan (IRP) should be continuously updated. In addition to the periodic review and update there should be a Post Mortem after each incident where the IRP is updated with lessons learned. The IRP is not a single document; therere should be a general IRP, as well as a specific IRP for each threat that scored high in the risk assessment. There should also be a requirement to create an IRP for any new threats as part of the Incident Post Mortem.
- Incident Response Plan:
- Develop a detailed incident response plan (IRP) with clear roles and responsibilities.
- Define specific procedures for handling different types of attacks, including DDoS, data breaches, and malware infections.
- Establish a communication protocol for notifying stakeholders, employees, and customers.
- Business Continuity and Disaster Recovery (BC/DR):
- Ensure that backup systems are in place and regularly tested to recover from DDoS attacks, ransomware, or data breaches.
- Develop and test business continuity plans for operational resilience during cyber incidents.
- Lessons Learned: After any security incident, conduct a post-incident review to identify areas for improvement.
Monitoring and Detection
Effective IT Security is not a set-it-and-forget-it proposition. The threat landscape is continuously evolving and continuous monitoring and early detection are key components to maintaining a strong security posture. The Risk Management Policy should outline the purpose for, minimum requirement of, and expected results of your organizations monitoring and detection efforts. Typically this will include:
- Security Information and Event Management (SIEM):
- Implement a SIEM solution for continuous monitoring, correlation, and analysis of security events across the network.
- Threat Hunting:
- Regularly conduct proactive threat hunting to identify potential threats before they escalate.
- Security Audits:
- Schedule regular internal and external audits to assess the effectiveness of cybersecurity measures.
- DDoS Detection:
- Implement real-time monitoring tools for identifying DDoS attack patterns, such as unusual traffic spikes or malformed packets.
- Performance Metrics: Define key performance indicators (KPIs) for the cybersecurity program, such as response and recovery times.
When defining key performance metrics try to focus on metrics within your control, and that promote the positive improvement you want to see. For example: while “Number of Attacks” is a tempting metric, it is both outside of your control (therefore not a measure of anything you are doing) and encourages under reporting incidents.
Training and Awareness
Employee Training is a critical aspect of any security policy, and this is never more true than at leadership positions. Consequently the requirement for Training and Security Awareness at all levels of the organization (not just within IT) is a critical component of the Risk Management Program.
- Employee Training:
- Conduct regular training on recognizing phishing emails, safe internet practices, and social engineering tactics.
- Run simulated DDoS and cyberattack drills to familiarize employees with response protocols.
- Security Awareness Program: Develop a continuous program to keep employees informed about new threats and best practices.
- Executive and Board-Level Awareness: Ensure that leadership understands the cyber risk landscape and is involved in high-level decision-making.
Compliance and Legal Considerations
While specific regulatory compliances are usually mentioned in the Executive summary they need to be a constant consideration for each subsequent section, and each subsequent document that comprises the Risk Management Policy. Furthermore an key, and often overlooked, aspect of this is maintaining a program to evaluate and mitigate any risks associated with using third party service, and ensuring that any third party processors remain compliant.
- Regulatory Requirements: Ensure that the cybersecurity program complies with relevant regulations (GDPR, HIPAA, CCPA, PCI-DSS).
- Data Privacy: Develop data protection policies in line with privacy regulations and ensure that sensitive information is adequately secured.
- Third-Party Risk Management: Assess the cybersecurity posture of third-party vendors and ensure contractual obligations around data security are in place.
The right amount of protection
While it is no small undertaking, a robust Risk Management Program will produce results that far exceed the efforts it takes to implement and maintain.
- You will be able to react to and recover from threats faster.
- You will be able to reduce both risk and security costs by focusing security efforts where they are most needed.
- And you will have ongoing assurance that your security efforts are producing real and measurable results.
2024 we saw some of the largest attacks to date. These included the Mirai botnet attack on an Asian hosting provider at over 2Tbps and one of the largest known DDoS attacks in Europe at 1.4Tbps, which was fully mitigated by Link11.
The frequency of DDoS attacks is also steadily increasing. Link11 has already seen an increase of over 26% in the first half of the year compared to the first half of 2023. Other providers are also seeing an increase in DDoS attacks of up to 60% in 2024. According to the ENISA Threat Landscape 2024, DDoS attacks are the most common threat in the EU and account for the largest share of cyberattacks analyzed between July 2023 and June 2024 at over 40%. They surpassed ransomware (25.8%) and data theft (19%). This development clearly shows how easy it is to carry out such cyberattacks and how readily available DDoS-as-a-Service is.
The impact of artificial intelligence
Although difficult to quantify, Artificial Intelligence (AI) is already being used in a wide range of cyber incidents. This is evidenced by the significant increase in the frequency of attacks, the enormous size of some of these DDoS attacks, and the orchestrated execution of multi-vector attacks. However, botnets and attacks are difficult to reverse engineer and tend to be transient in nature, making accurate analysis difficult.
Risk management and compliance will become more important
In 2024, there was a trend towards agile risk management, in which organizations can respond quickly to new cyber threats, including DDoS attacks. Advanced data analysis and AI-based risk assessment tools are increasingly being used to identify potential vulnerabilities and automate compliance monitoring.
Learn more about a GDPR-compliant, cloudbased and patented DDoS Protection that delivers, what it promises.
Outlook for 2025: New targets, more monitoring, stronger attacks
Shift in Targets: Traditional sectors such as gaming and financial services remain vulnerable, and the motivation for politically motivated attacks on governments and critical infrastructure remains high. At the same time, new industries such as cryptocurrencies and biotechnology are increasingly becoming the focus of attackers. This development shows that attackers are increasingly turning their attention to industries with high-value assets and sensitive business processes.
Bigger and badder: DDoS attacks will continue to increase in size, frequency and sophistication. Advanced techniques will continue to be used alongside more typical volumetric vectors to take advantage of the ever-increasing backbone and enterprise network capacity. The proliferation of IoT and improved botnet capabilities will result in more attacks regularly exceeding 200Gbps.
Importance of observability: Organisations will dig deeper into their operations to better monitor their IT stacks (whether on-premises, cloud or hybrid) to better understand the impact of cybercrime. The focus is not just on protecting the perimeter, but also on measuring impact and workload to meet regulatory requirements and to better understand the impact and vulnerabilities during an attack. The overall goal is to improve end-to-end security.
Growing importance of API inventory: A growing problem for organisations will be the lack of visibility into their API landscape. As the number of APIs used both internally and externally grows, organisations will lose sight of the big picture. In 2025, organisations will increasingly rely on a comprehensive inventory of their APIs to identify vulnerabilities, meet compliance requirements and reduce the cost of API management.
Cyber insurance on the rise: Faced with an ever-evolving threat landscape and the increasing possibility of business interruption and customer loss, organisations will increasingly purchase cyber insurance to mitigate these risks. In addition, increasing regulatory pressure and the need to reduce potential legal and financial liability will prompt companies to take a hard look at their business processes and weigh the risk of an uninsured event.
The bottom line
The threat from DDoS attacks remains serious. Organisations need to be prepared for the constant evolution of attack methods and adapt their security measures accordingly. Investing in advanced technologies such as DDoS protection solutions, enhanced monitoring and a robust risk management and compliance framework is essential to protect against this threat.
Distributed Denial-of-Service (DDoS) attacks present a technical challenge for Internet Service Providers (ISPs), requiring comprehensive strategies to protect their WAN and customer networks. This article discusses the key issues and practical solutions for robust DDoS protection.
Uplink to a DMP (DDoS Mitigation Provider)
Effective DDoS protection begins with an uplink to a DDoS Mitigation Provider (DMP) that can filter traffic for the customer using Border Gateway Protocol (BGP). This solution allows incoming traffic to be analyzed and malicious streams to be intercepted before they reach the ISP’s network. By integrating BGP, traffic can be selectively rerouted and cleaned, enabling an efficient and rapid response to DDoS attacks. There are several ways to achieve this:
- Standby Protection
A flexible DDoS protection system should be able to route networks on demand. This means that specific network segments can be redirected to a DMP on an as-needed basis to ward off attacks. This “standby protection” provides a cost-effective solution because resources are only used when an actual attack occurs. However, the NMC (Network Management Center) must first detect a DDoS attack and decide whether to respond.
- Always-On Protection
For highly critical networks, continuous monitoring and protection by the DMP is recommended. With this “always-on” strategy, all network traffic is continuously routed through the DMP to be prepared against DDoS attacks at all times. This method provides the highest level of protection, ensuring that attacks are immediately detected and mitigated.
- Monitored Standby
Another effective strategy is monitored standby, where networks are monitored by flow and automatically redirected in the event of an attack. This approach combines the benefits of standby and always-on protection. Networks are continuously monitored, and when an attack is detected, traffic is automatically redirected to the DMP to counter the attack. Monitoring systems should either notify the relevant Operations (OPS) or Network Management Center (NMC) team and allow them to decide, or automatically reroute the network of the targeted IP through the DMP network using BGP.
Learn more about a GDPR-compliant, cloudbased and patented DDoS Protection that delivers, what it promises.
Tenant-Capable System
A modern DDoS protection system must be tenant-capable, meaning it must support the management of multiple customers (tenants) within a single system. This multi-tenant capability allows ISPs to protect and manage different customers and their networks individually without compromising security or performance.
User Access Management
Another critical aspect is User Access Management, which provides various configurations and management options for users. ISPs need to control access to the DDoS protection system and assign different rights and functions to users. This includes managing settings, monitoring, and taking countermeasures.
Conclusion
DDoS protection is a multifaceted challenge for ISPs. Implementing an uplink to a DMP, using standby and always-on protection, monitoring and automatic rerouting during attacks, tenant-capable systems, and effective user access management are essential. These strategies provide a streamlined, efficient approach to DDoS protection that ensures continuous service availability and customer satisfaction.
The IT world is full of interconnected systems, and APIs (application programming interfaces) are the glue that holds them together. But what happens when that glue becomes a vulnerability?
A fictional scenario, a real problem
Imagine a situation where an organization’s systems suddenly start sending sensitive data to an unknown location. This seemingly anomalous event could point to a compromised API – a software intermediary that facilitates communication between different components. While APIs are critical to functionality, a lack of visibility into their capabilities can create security gaps and leave them vulnerable to exploitation.
Learning from the T-Mobile example
The above scenario is not just hypothetical. Large organizations, such as T-Mobile in the US, have faced the harsh reality of API breaches. In fact, T-Mobile has been targeted multiple times in recent years, with incidents resulting in the exposure of millions of customer records. This highlights the growing trend of attackers focusing on APIs as potential entry points.
A Look Back at T-Mobile’s Breaches
T-Mobile’s case illustrates the significant impact of API violations. Here’s a breakdown of some of their known incidents:
- January 2023: An API vulnerability exposed the personal information of 37 million accounts.
- August 2018: Data from 2 million subscribers was stolen, possibly through an API exploit.
These are just two examples, and it’s important to note that the full extent of API-related breaches may be underreported.
Beyond data loss: Legal and Reputational Damage
The impact of API breaches goes far beyond compromised data. T-Mobile faced legal repercussions, including a large settlement in 2021 and a class action lawsuit in 2023. This highlight the potential for significant financial penalties associated with inadequate data security practices.
Contact our experts and find out how your business can be protected with an automated security solution.
Turning the Tide: Securing Your APIs
The good news is that organizations can learn from these incidents and take proactive steps to secure their APIs. Here are some key takeaways:
- Implement strong access controls: Authentication and authorization mechanisms ensure that only authorized users have access to sensitive APIs.
- Monitor for anomalies: Use tools that can detect unusual activity and flag potential API misuse.
- Regularly assess API security: Conduct thorough assessments to identify and remediate any vulnerabilities within your API ecosystem.
By adopting these practices, organizations can significantly strengthen their security position and mitigate the risk of API-related breaches.
Looking ahead
The T-Mobile case serves as a stark reminder: APIs are powerful tools, but they require careful attention to security. By prioritizing API security, organizations can protect their data, avoid hefty fines, and maintain customer trust in the digital age.
At Link11, we advise implementing a content filter and tagging mechanisms in front of each site to detect unknown APIs and stop unknown users. This, combined with authentication and rate limiting to prevent resource abuse, and reporting, will help alert security teams to anomalies even for unknown APIs.
Are you ready to take the security of your APIs to the next level? Schedule a consultation with our experts and discover how our solutions can protect your applications.
Distributed Denial-of-Service (DDoS) attacks are a major challenge for hosting providers and require comprehensive strategies to protect their infrastructure and underlying customers. This article examines the key issues hosting providers face and practical solutions for robust DDoS protection.
The Role of Transit Providers
A transit provider is an essential part of Internet traffic flow. As such, its focus is on protecting its networks and network segments. However, this can also be a vulnerability for the host. It is crucial to ensure that your own transit providers have DDoS mitigation strategies in place. This requires close collaboration with transit providers. To understand the defenses and their impact on your systems, you need to look at the problem from the transit provider’s perspective. Most transit providers always offer standard DDoS protection.
In the standard package, however, this is just a “blackhole” service that simply drops all traffic to the attacked IP address (or IP range). If the underlying clients are KRITIS companies, this becomes a problem for the host provider. The rationale behind this strategy is that any transit provider’s first priority is to protect its capacity in the region. The concerns of the host provider in that region are secondary.
Uplink or Capacity Management
Uplink capacity at the host provider’s site is critical for managing traffic volumes, especially during a DDoS attack when traffic increases dramatically. Hosting providers must invest in high-capacity uplinks and maintain sufficient reserves to effectively handle these traffic spikes. A multi-ISP strategy is therefore adopted, which takes into account the traffic that the DDoS brings and also an appliance that can effectively handle the DDoS traffic so it does not exceed the maximum capacity limit (scalability).
Reselling protection services
DDoS protection services can be expensive. For example, transit providers resell their blackhole DDoS protection to reduce appliance and maintenance costs on their end. Hosting providers can also reduce these costs by reselling either their own protection services or white-label products to customers. This strategy not only offsets costs but also adds value to the provider’s offering and builds customer loyalty. But how can this be presented to the customer? IPS/uplink provider protection cannot be presented in the same way. Another challenge is how to address the issue of buying a local appliance.
Expertise and cost of ownership
Effective DDoS mitigation with appliances requires skilled professionals who can respond quickly. Maintaining this expertise is costly and requires a balance between hiring costs and the need for robust protection. Ongoing training is essential to stay ahead of evolving threats. It’s worth mentioning, too, that the capacity of the access line is not scalable, even with a local appliance.
Appliance, the “on-premise” device
Appliances allow you to intervene directly in the data stream, depending on the location and local infrastructure. These devices are expensive to purchase and require specialized configuration and maintenance. They also have an end-of-life date and the capacity of the access line is limited and difficult to customize. Regular updates and monitoring are required to remain effective against new attack vectors, requiring ongoing investment in technology and training. This makes it a complicated and costly solution.
Cost Management and Billing
The financial impact of DDoS protection, including transit and mitigation services, is significant. Effective cost management requires careful planning and budgeting. Providers need to monitor their usage and optimize their spending to avoid unexpected and high bills.
Learn more about a GDPR-compliant, cloudbased and patented DDoS Protection that delivers, what it promises.
Transparency through reporting
Customers expect transparency around security measures. This starts with the small customer and goes hand-in-hand with KRITIS organizations and other stakeholders. Regular, detailed reporting on DDoS attacks and mitigation is essential. These reports build trust and demonstrate the provider’s commitment to protecting customer data and services.
A DDoS mitigation provider…
…should offer an improvement and simplification of protection in these areas. This enhancement can provide a robust solution to improve DDoS protection through carrier-neutral peering and Border Gateway Protocol (BGP) routing. This configuration enables efficient traffic routing and redirection during attacks, providing redundancy and increased resilience.
This is achieved through an automated, real-time DDoS protection service, including reporting of DDoS attacks over IP and reduction of processes and steps in hosting operations. This automation reduces the burden on hosting providers, allowing them to focus on their core business while ensuring robust security.
Conclusion
Protecting against DDoS attacks is a multi-layered challenge for hosting providers. Solving issues related to transit providers, uplink capacity, reselling protection services, cost management, transparency through reporting, maintaining expertise, and on-site equipment maintenance are all essential. The implementation of vendor-neutral peering and BGP routing further increases resilience. Automated and scalable solutions provide an optimized, effective approach to DDoS protection and ensure continuous service availability and customer satisfaction.
A hosting provider offers services that enable individuals and businesses to host websites and applications on the Internet. These companies provide the infrastructure and technical resources needed to ensure that websites and applications are continuously available and operational. This includes a variety of hosting services, from basic shared hosting to more complex solutions such as cloud hosting and managed hosting.
Types of hosting services:
- Shared hosting: Multiple websites share the resources of a single server. This is suitable for smaller websites with low traffic.
- VPS hosting: A physical server is divided into virtual servers, each operating independently, providing more control and resources than shared hosting.
- Dedicated hosting: An entire server is reserved exclusively for one customer, providing maximum control and security.
- Cloud hosting: Hosted on a distributed cloud infrastructure, providing redundancy and scalability.
- Managed hosting: The provider handles server management, including updates, security, and backups, ideal for customers who prefer to focus on their business operations.
Infrastructure and Technologies
Hosting providers operate high-performance servers, redundant networks, and advanced security measures in distributed data centers. Modern technologies such as load balancing, virtualization, and containerization are often used to ensure a reliable and scalable environment.
Security and Support
Security is paramount in hosting. Providers implement measures such as firewalls, DDoS protection, malware scanning, and regular security updates. Customer support is often available 24/7, and service level agreements (SLAs) define service availability and reliability, setting clear expectations for the quality of hosting services.
Data Center Providers: The backbone of modern IT
A data center provider offers specialized infrastructure services so that enterprises can operate their IT assets in secure, highly available, and high-performance data centers. This includes the physical environment and technical resources needed to host and manage servers, networks, and storage systems.
Types of data center services:
- Colocation: Customers lease space in a data center to house their own servers and network equipment. The provider offers infrastructure, cooling, power, and physical security.
- Managed hosting: The provider assumes responsibility for managing and maintaining the IT infrastructure, allowing companies to focus on their core business.
- Cloud services: Data center providers offer cloud computing services that enable businesses to scale computing resources on demand, including Infrastructure-as-a-Service (IaaS), Platform-as-a-Service (PaaS), and Software-as-a-Service (SaaS).
Infrastructure and Technology
Modern data centers are equipped with redundant power systems, uninterruptible power supplies (UPS), backup generators, and advanced cooling systems to ensure maximum availability. They have high-performance networks with multiple redundant connections to multiple Internet Service Providers (ISPs).
Learn more about a GDPR-compliant, cloudbased and patented DDoS Protection that delivers, what it promises.
Security measures
Data center providers make protecting their customers’ IT assets a top priority. They implement comprehensive physical security measures such as strict access control, video surveillance, and biometric scanners, as well as network security measures such as firewalls and intrusion detection systems (IDS). They also provide backups, data encryption, and disaster recovery solutions to ensure data integrity.
Compliance and certifications:
Data center providers often adhere to strict compliance requirements and hold certifications such as ISO 27001 (information security management), PCI-DSS (credit card data security standards), HIPAA (healthcare privacy standards), and SOC 1/2/3 (datacenter security audits).
Customer Support and SLAs:
Like hosting providers, data center providers offer around-the-clock support and service-level agreements (SLAs) that guarantee high availability and performance. This gives businesses the confidence and support they need to run their IT operations optimally and securely.
The bottom line
Both hosting and data center providers play critical roles in the modern IT landscape. Hosting providers ensure the availability and security of websites and applications, while data center providers offer world-class infrastructure for IT resources. Through a combination of advanced technology, robust security measures, and reliable support, they help businesses manage their digital assets securely and efficiently, enabling them to achieve their business goals.
Despite a massive and sustained DDoS attack, Link11 was able to protect the client’s critical IT infrastructure. The attack was notable not only for its public target, but also for the methods used by the attackers. Below we take a closer look at the technical aspects of this attack.
Multi-stage attack tactics
The attack tactics were multi-stage, starting with smaller, barely noticeable attacks that were cleverly integrated into normal traffic. These preparatory attacks were likely used to probe the system and identify potential vulnerabilities. This was followed by a massive attack that lasted almost exactly 24 hours.
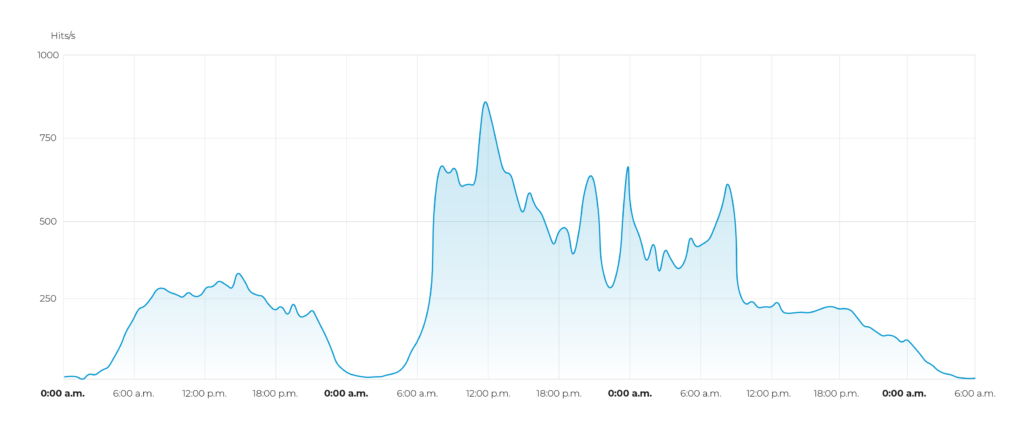
Attacker obfuscation techniques
The attackers used a sophisticated technique to disguise their attack. They mimicked normal traffic so closely that the malicious activity was initially difficult to distinguish from legitimate traffic. A detailed analysis of the data was required to detect the manipulation of the traffic.
Attack Dynamics and Captcha Analysis
The attack had an unprecedented dynamic. The intensity of the attack reached a level within a very short period of time, indicating a precise and well-orchestrated action. A detailed analysis of the HTTP protocol shows that the activity is malicious. Traffic analysis revealed that a large proportion of requests were valid, but a strikingly high proportion were erroneous. The imbalance in the ratio of correct to incorrect requests clearly indicates that the protocol is being manipulated by malicious actors.
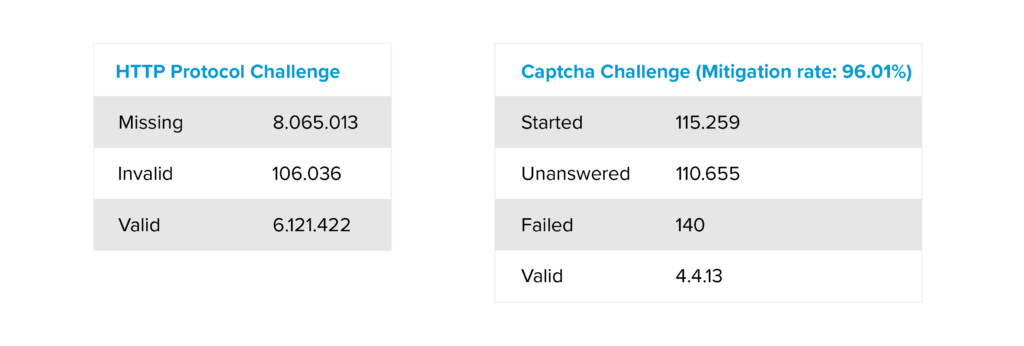
The analysis of the CAPTCHA results was particularly revealing. While a high CAPTCHA success rate would normally be expected for legitimate traffic, in the case of this attack, the success rate was only four percent. This drastic decrease suggests the use of bots. It should be noted, however, that the visual challenge alone is not the deciding factor.
Although some bots are able to solve the visual challenge, other parameters are also included in the evaluation, such as the speed of the solution or the pattern of mouse movements during the interaction. In particular, highly developed bots that execute JavaScript and actually solve the visual challenge could meet some of these requirements. However, the low success rate combined with the high number of failed HTTP requests clearly indicates a coordinated botnet attack.
The attack tactics in detail
The attack was very complex and persistent. The attackers used a multi-stage strategy to achieve their goals:
- In the reconnaissance phase, a large number of small attacks were first carried out to probe the system and identify potential vulnerabilities. Such attacks often go unnoticed because they can be hidden in legitimate traffic.
- The main attack occurred after the preparation phase and consisted of a massive DDoS attack that lasted almost 24 hours. The attackers used a large number of compromised devices to generate massive amounts of traffic. At the same time, there was no impact on the performance of the business.
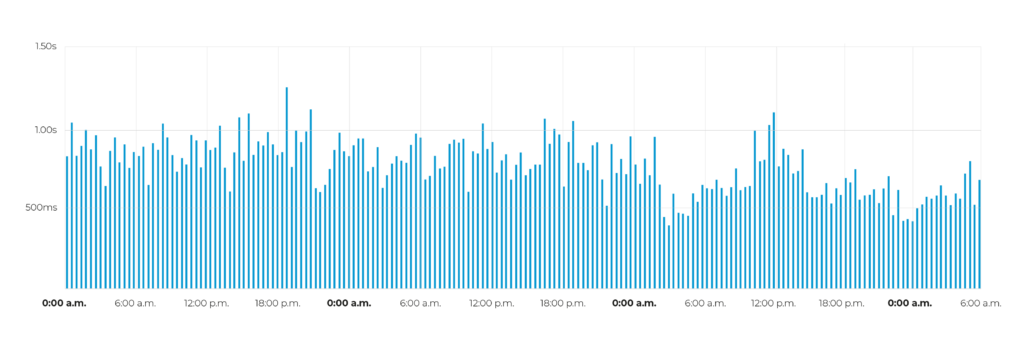
- Traffic manipulation: To hide the attacks, the attackers mimicked legitimate traffic. However, analysis of the HTTP protocol revealed anomalies such as a high number of erroneous requests.
Indications of a Cybercrime-as-a-Service attack
The precise duration of the attack – almost exactly 24 hours – leads us to conclude that this was a cybercrime-as-a-service attack. DDoS attacks are often offered as a service on the darknet, with clearly defined time frames for carrying out the attacks. The cost depends on the duration, target, and complexity of the attack. The 24-hour period observed in this case corresponds exactly to one of the common offers on the darknet, which further supports the assumption of a commercially acquired attack.
A look at price lists on the darknet shows that a 24-hour DDoS attack against an unprotected website with a bandwidth of 10,000 to 50,000 requests per second can be purchased for around 35 US dollars. However, for a more sophisticated attack against a protected site using multiple elite proxies, the cost can quickly rise to $170 or more. Given the size and duration of the attack, it is likely that the attackers were willing to spend more to cause maximum disruption.
Origin of the attack
The network distribution was analyzed to distinguish between two common scenarios: the use of rented bots and the use of compromised devices. Rented bots typically show a concentration on a few large cloud providers. In contrast, this attack showed a broad distribution of attacks across many small networks. This pattern is characteristic of botnets made up of a large number of compromised home devices. The fact that the attacks originated from 110 different countries underscores the global reach of this botnet and makes it difficult to determine the exact origin of the attack.
Conclusion
The DDoS attack highlights the need to protect against such attacks. Organizations must continuously monitor and keep their IT infrastructure up to date. It is also important to be aware of the risks posed by botnets.
What can you do?
- Regular security checks
- Investment in a high-performance DDoS protection solution
- Raising employee awareness
- Partner with an experienced IT security provider
While the digital landscape has always been subject to change, the rapid shifts of the last few years have made this more obvious than ever. Cyberattacks are becoming increasingly sophisticated and come in a variety of forms, and cybercriminals are using increasingly sophisticated methods to attack companies and steal sensitive data. This results in high financial losses and reputational damage.
The German industry association Bitkom has published alarming figures: the damage caused by cybercrime to the German economy amounted to more than 178 billion euros in the past 12 months. This is around 30 billion more than in 2023 and underlines the urgency of taking effective protective measures. To respond to this, companies must continuously adapt their security strategies.
Artificial intelligence (AI) is not only revolutionizing our working world, but also cybercrime. According to a recent Darktrace study, German companies are particularly poorly prepared for AI-based attacks. While 60% of companies worldwide state that their existing security measures are not designed for AI-based attacks, this figure is 78% in Germany.
Although German companies are lagging behind in the detection of and defense against AI-driven threats, innovative solutions already exist. These make it possible to detect, analyze and defend against threats more quickly. This makes companies more resistant to cyberattacks.
The limits of traditional security solutions
Traditional security solutions are reaching their limits when it comes to keeping up with the speed and complexity of modern cyberattacks. Signature-based detection methods are often too slow to fend off new threats, and manual analysis is time-consuming and prone to error.
AI as a driving force for innovation in cybersecurity
AI, especially machine learning (ML), offers several benefits that complement and enhance traditional security solutions:
- Proactive threat detection: AI algorithms can analyze vast amounts of data and identify patterns that indicate potential attacks. This allows threats to be detected at an early stage and countermeasures to be initiated.
- Automation of routine tasks: Tasks such as log analysis, vulnerability detection and incident response can be automated, freeing up human experts to focus on more strategic tasks.
- Adaptability: AI models can continuously adapt to new threats by learning from new data. This makes them a robust and future-proof solution.
- Precision: AI-based systems can recognize complex correlations and thus reduce false alarms.
Contact our experts and find out how your business can be protected with an automated and AI-based security solution.
How AI helps in the defense against cyberattacks
- Anomaly detection: By comparing current data with historical data, AI systems can identify deviations that indicate a possible attack.
- Malware detection: AI algorithms can detect malware based on its behavioral characteristics, even if it is not yet contained in a virus database.
- Phishing detection: AI-based systems can detect phishing emails with high accuracy by using natural language processing and machine learning.
- Incident response: AI can assist in the investigation of security incidents by automatically collecting and analyzing relevant data.
Challenges and future of AI in cybersecurity
Stjepan Picek, cybersecurity expert at Radboud University, emphasizes the importance of decentralized learning paradigms, such as federated learning and split learning, to increase the security of AI systems. These approaches make it possible to train AI models on multiple devices without having to transfer the raw data to a central server. This minimizes the risk of data leaks and breaches.
Generative AI, especially large language models (LLMs), harbors both great potential and risks. While LLMs can be used to create high-quality content, they can also be misused to generate deepfakes and other types of disinformation.
The automated analysis of large amounts of data by AI will play a decisive role in the detection of and defense against cyberattacks in the future. By automating routine tasks, security teams can focus on more complex tasks, in turn increasing the efficiency of defensive measures.
Conclusion
AI offers enormous potential to strengthen cybersecurity. With the ability to analyze large amounts of data in real time and recognize complex patterns, AI-based systems can detect and defend against threats faster and more precisely. Companies that invest in AI-based security solutions can significantly increase their resilience to cyberattacks and ensure business continuity.
Want to future-proof your business IT and protect against cyberattacks? Contact us today to learn more about how AI-based security solutions can help you optimize your cybersecurity.
Artificial intelligence (AI) has become a powerful tool that both enriches our lives and poses new threats. From healthcare to the financial industry, from manufacturing to entertainment, AI-based applications are revolutionizing the way we work and live. But the flip side of this coin is the increasing complexity of cyber threats. While AI is driving innovation in many areas, it is also being misused by cybercriminals to amplify and automate their attacks.
ChatGPT and co.: AI as a door opener for cyber criminals
Language models such as ChatGPT have dramatically lowered the threshold for cybercrime. With just a few prompts, even laypeople can write convincing phishing emails, develop malware, or spread targeted disinformation. Although these models are generally programmed in such a way that they do not produce illegal content, so-called jailbreaks make it possible to circumvent these restrictions. Unmoderated chatbots such as FraudGPT, which are explicitly trained for criminal purposes, also exist on the darknet.
Companies in a quandary
The growing threat of AI-based attacks is putting companies under pressure. A study by Sopra Steria shows that the majority of companies consider the risk of AI-supported cyberattacks to be high. At the same time, many companies also see artificial intelligence as an opportunity to strengthen their own cybersecurity.
AI as a double agent: attack and defense
AI is a Janus face that offers both protection and danger. On the one hand, it can be used as a powerful tool to defend against cyberattacks. Anomaly detection, malware analysis and incident response are just a few examples of how AI can improve the security of IT systems. On the other hand, AI can be misused by hackers to refine and automate their attacks.
- Adversarial attacks: AI systems can be systematically deceived by deliberately manipulating input data. A simple example: a self-driving car can misinterpret a road sign by placing small disturbances on it that are barely perceptible to the human eye.
- Deepfakes: Creating hyper-realistic, fake videos and audio has become affordable and easy. Deepfakes can be misused for disinformation campaigns, blackmail and identity theft.
- AI-powered phishing attacks: By analyzing large amounts of data, attackers can create highly personalized phishing emails that significantly increase the likelihood of success.
Challenges for IT security experts
The integration of AI into cybersecurity poses a number of challenges:
- Black box problem: Many AI models are so-called black boxes, i.e. their decisions are difficult for humans to understand. This makes it difficult to identify vulnerabilities and develop defensive measures.
- Arms race: The race between attackers and defenders is further intensified by AI. New attack methods are constantly being developed while defense systems are generally reactive rather than proactive.
- Ethical issues: The use of AI in cybersecurity raises ethical issues, such as the risk of surveillance and the development of autonomous weapons systems.
Contact our experts and find out how your business can be protected with an automated and AI-based security solution.
The way forward
To minimize the risks of AI and reap its benefits, IT security experts need to consider the following aspects:
- Red Team vs. Blue Team: Organizations should conduct regular Red Team exercises to test the resilience of their systems against AI-based attacks.
- AI-based defense: The use of AI to defend against AI attacks is a logical step. However, these systems must be continuously monitored and updated.
- Transparent AI: It is important to develop AI models that are transparent and interpretable. This makes it possible to better understand the decisions they make and identify potential sources of error.
- Collaboration: Collaboration between researchers, developers and security experts is crucial to ensure the security of AI systems.
- Regulation: Appropriate regulation is needed to guide the development and use of AI and ensure that it is used for the benefit of society.
Conclusion
The integration of AI into cybersecurity is a complex issue that presents both opportunities and risks. To reap the benefits of AI, we need to approach the associated challenges with an open mind and work continuously to improve security measures. The future of cybersecurity will be significantly shaped by the development of AI and our changing understanding of its ethics.