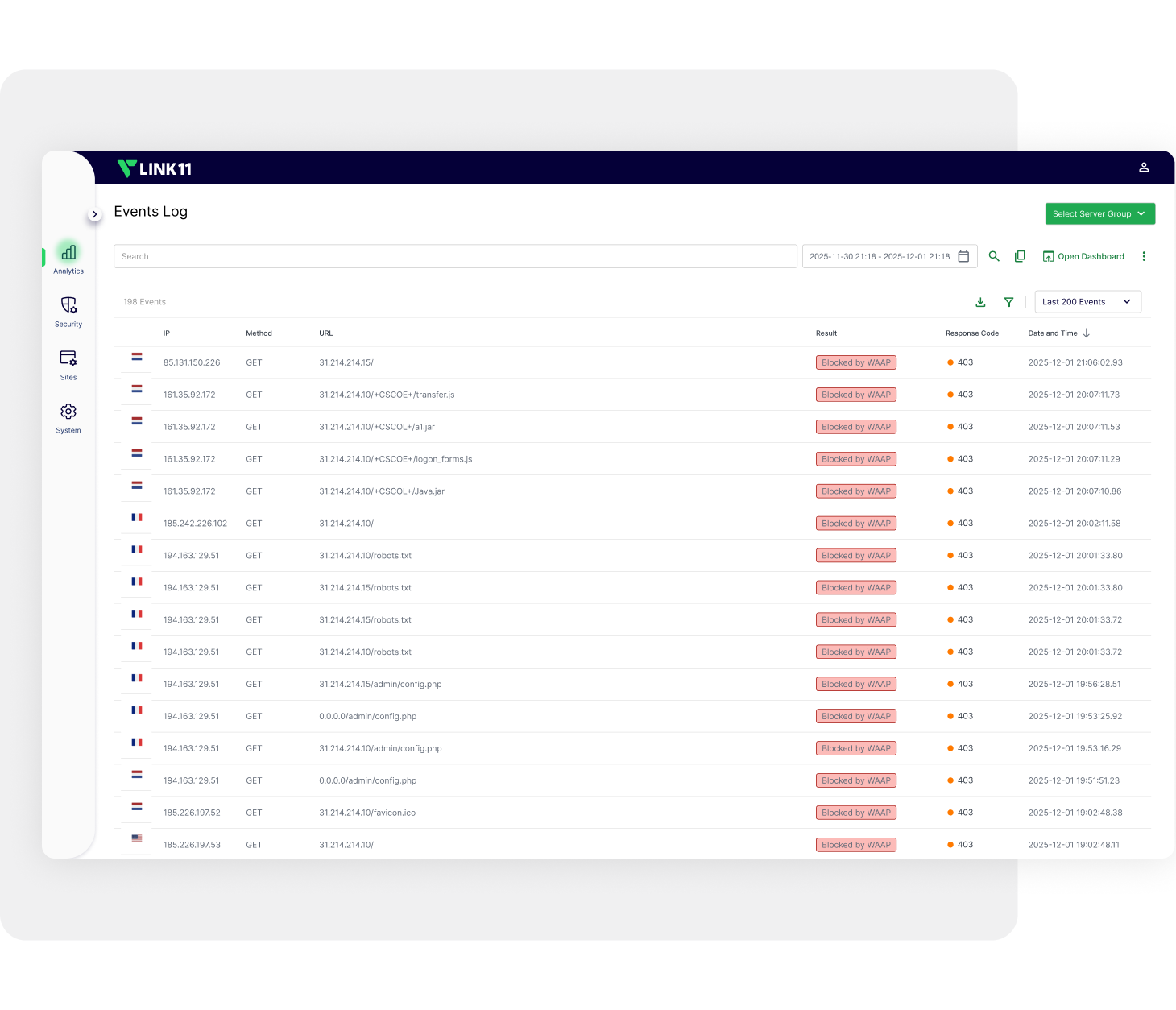
Web Application Firewall
Always-on protection blocking SQLi, XSS, and CSRF; covering OWASP Top 10 and exploits; hardening sessions/cookies with real-time zero-day defense.
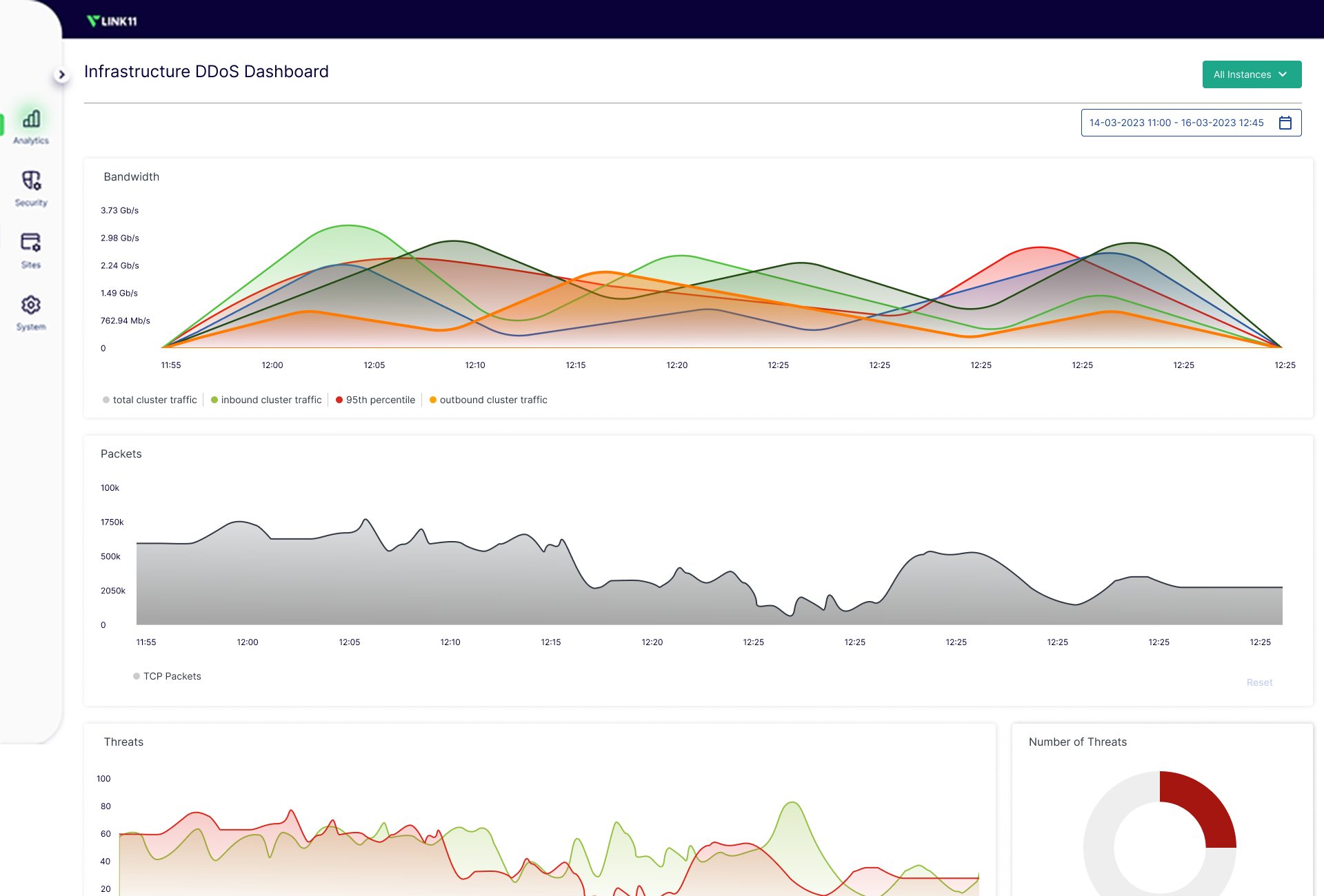
Your shield against known and unknown attacks
Instead of relying solely on traditional methods, such as IP blocking or signature detection, WAF provides you with an intelligent protection concept: Suspicious content is analyzed in real time, access is controlled in a targeted manner, and dangerous entries are blocked immediately. Whether account takeover attempts, zero-day exploits, or malicious payloads — you can rest assured that your applications are effectively protected at all times.
Web applications are the Achilles heel in many defenses
-
40%
Of all cyberattacks target web applications directly.
-
86%
Of all web applications contain at least one vulnerability.
-
96%
Of all attacks on web applications can be prevented with WAF rules.

Comprehensive protection in real time – flexible, adaptive, and precise against threats
-
Comprehensive threat protection
Comprehensively protect web applications against the OWASP Top 10—the world’s most critical security risks—and a wide range of other common attack vectors. A powerful combination of precise signature detection and intelligent heuristic analysis reliably identifies threats and blocks them in real time.
-
Ready to use
Thanks to preconfigured rules and signatures, you get immediate protection without having to invest valuable time in complex setup or lengthy fine-tuning. The solution is ready to use right out of the box and defends against threats in real time, allowing you to focus on your core business.
-
Adaptive security
Regular signature updates ensure your protection is cutting edge. New threats and attack methods are continuously analyzed, and defense mechanisms are automatically adjusted. This means your security infrastructure is constantly evolving — without any extra effort on your part.
-
Flexible policy control
With granular policies (ACLs) and customizable rules, administrators have full control over security policies. This allows you to tailor protection precisely to the requirements of individual applications, from selectively allowing trusted sources to blocking suspicious activity.
-
Zero-day protection
Targeted application whitelisting and precise validation stop malicious traffic before signatures are even available. This proactive strategy protects your applications against completely new, unknown attack methods and ensures constant availability.
-
Verifiable false positives
The sophisticated detection logic accurately distinguishes between real threats and normal user behavior. This reduces false alarms without affecting legitimate users. The result: maximum security without compromising the user-friendliness or performance of your services.
Web Application Firewall (WAF) –
Stop threats before they cause damage
We continuously monitor the internet for new vulnerabilities and threats. If a new threat is detected, your platform is automatically updated with the appropriate protective measures—quickly, reliably, and without any action on your part.
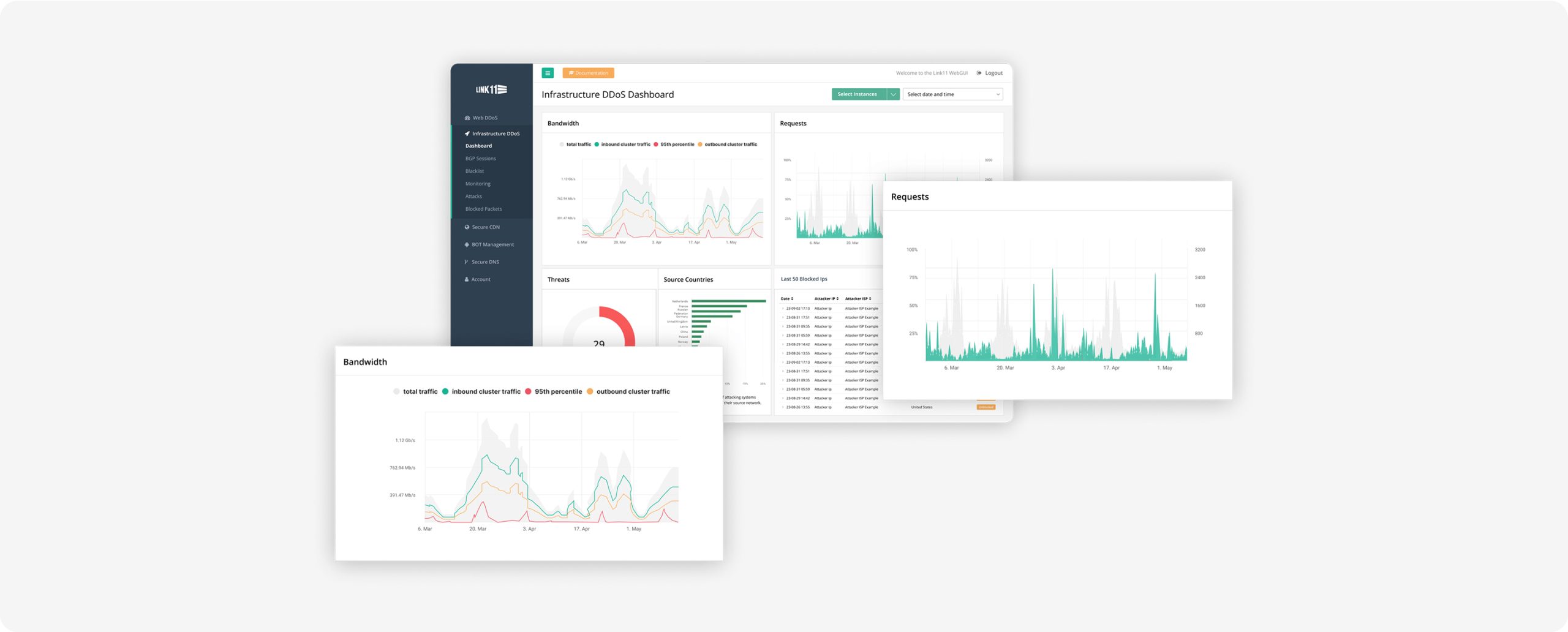
Application whitelisting
Zero-day exploits are successfully blocked because only traffic that complies with precisely defined, finely tuned application rules is allowed. This makes it virtually impossible for attackers to inject malicious code.
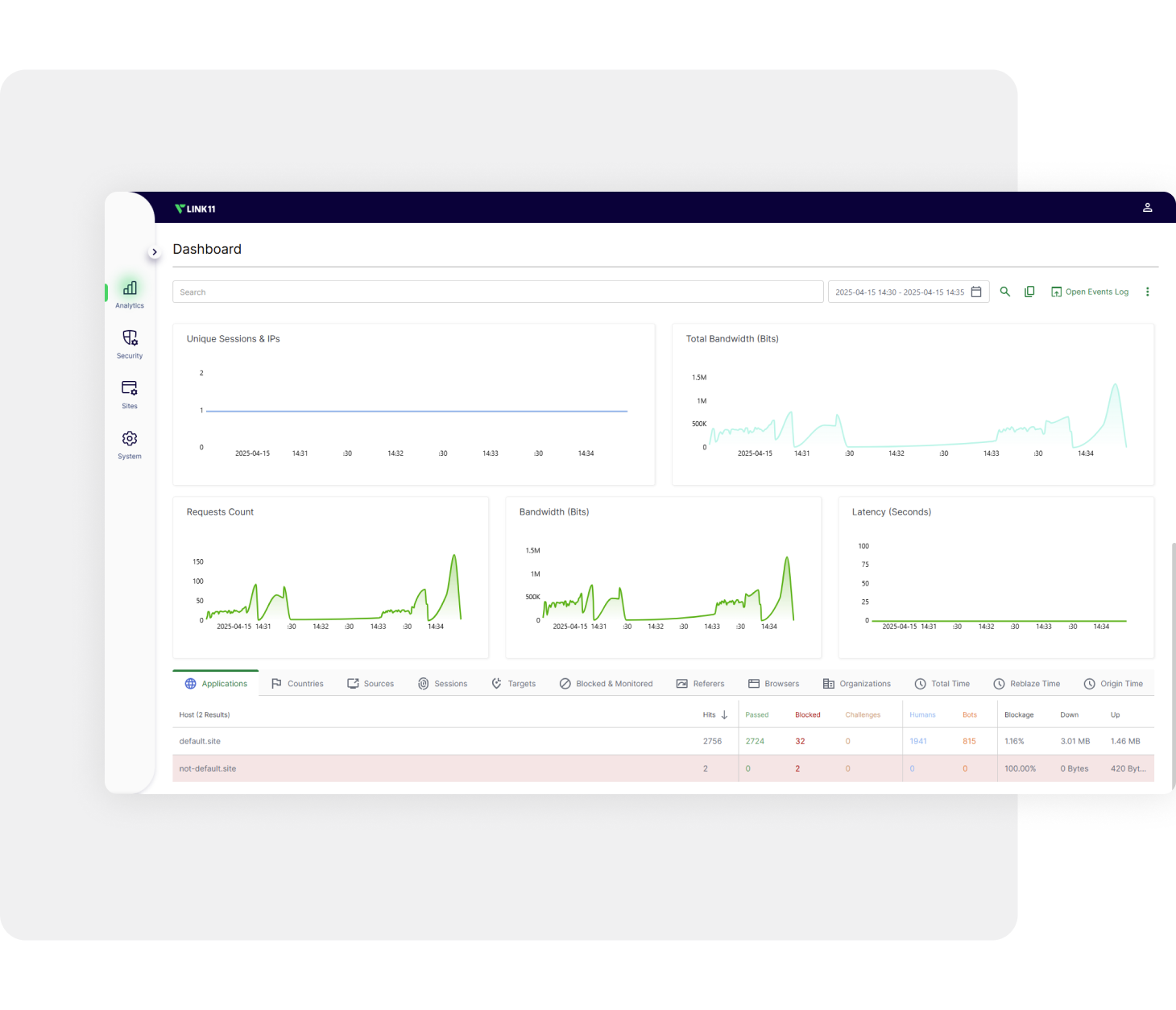
Precise administration tools
Maintain full control over your data traffic. With our unique access control technology, you can specify which countries, cities, networks, companies, anonymization services, or cloud and data center environments are allowed or blocked.
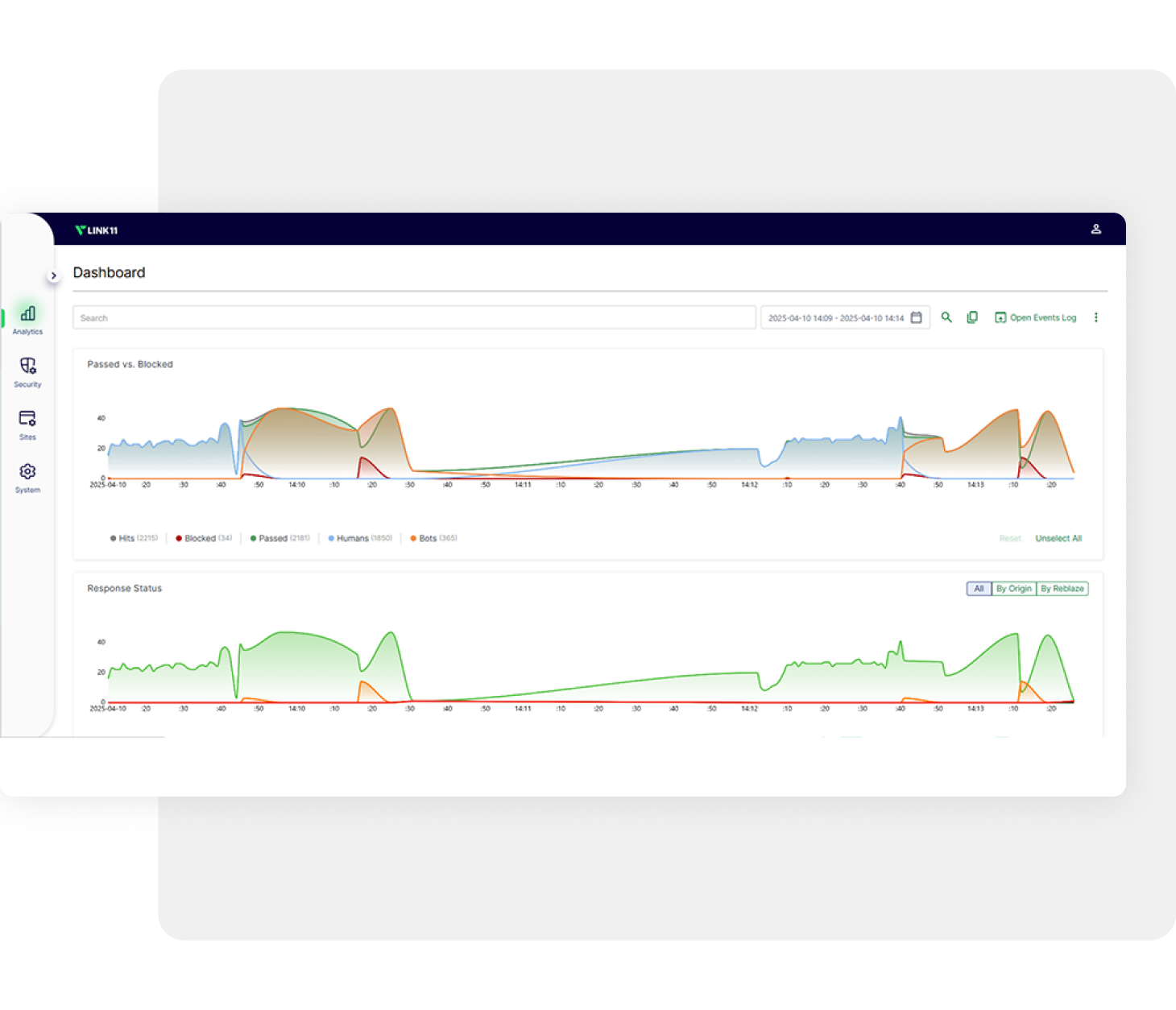
Biometric analysis
Using state-of-the-art biometric analysis, Link11 detects early on when attackers are scouting your system—for example, through penetration tests, reverse engineering, or automated scans. These activities are automatically stopped before any damage can be done, keeping your applications and data fully protected—without you having to lift a finger.